Japan Weekly Threat Report Feb 1-14
- 6 hours ago
- 4 min read
Author(s): Unit Zero Threat Research Team
🚪 Initial Access Broker (IAB)

Activities in the period targeted Japanese financial and industrial sectors, with sales of compromised access credentials and vulnerabilities on forums key listings emphasized high-value entry points for further exploitation. Our Unit Zero research team identified this possible victim according to the threat actor claims the Japanese bank in question appear to be Oita Bank, Ltd.
February 10: Sale of access to a Japanese bank for $5000 claimed with a networth of 48 million USD network vulnerability. (unnamed major institution) on advertised by an anonymous IAB as including RDP credentials and exploited zero-day entry; priced at premium for espionage or ransomware prep, no buyer confirmed but ties to Chinese APTs suspected.
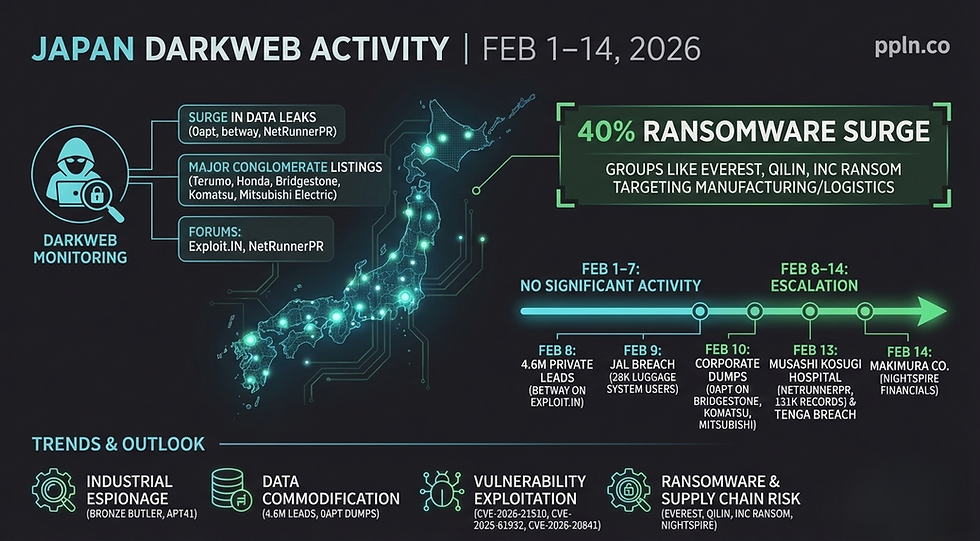
🔍 Japan Darkweb Activity
In the period from February 1 to February 14, 2026, darkweb monitoring revealed increased listings and illicit sales targeting Japanese entities, primarily via platforms like Exploit.IN forums. Activities focused on corporate data dumps, personal lead sales, and healthcare breaches, with no significant government leaks observed but one major hospital incident. Escalation was noted mid-February, dominated by threat actors like 0apt and threat actor 'betway'
February 4: Terumo Corporation (medical devices) listed by 0apt on darkweb forums, potentially involving operational or customer data.
February 8: Honda Motor Co. (automotive) listed by 0apt on darkweb forums; separate sale of 4.6 million private Japanese leads on Exploit.IN by betway, sourced from high-budget credit card campaigns in fashion, automotive, and finance sectors—data includes personal details for mailings and dumps.
February 10: Bridgestone (tires/manufacturing), Komatsu Ltd. (construction machinery), and Mitsubishi Electric (electronics) listed by 0apt on darkweb forums, indicating possible exfiltration of industrial data.
February 12: NetRunnerPR claimed breach of Nippon Medical School Musashi Kosugi Hospital, exfiltrating 131,135 patient records (names, IDs, contacts, personal details)
February 12: Stanley Autenrieth Auction Group listed by worldleaks on darkweb forums, with potential auction-related financial data exposure, though indirect ties to Japan.
These activities underscore industrial targeting for espionage or commodification, with 0apt prominent in corporate listings. Limited forum chatter on new tooling or recruitment specific to Japan.
🔒 Japan Ransomware Victims
Ransomware incidents against Japanese organizations showed a modest rise in the reviewed period, with groups like Nightspire, INC Ransom, Everest, and Qilin exploiting manufacturing, logistics, and industrial sectors. Victims included engineering, logistics, and manufacturing firms. Confirmed cases from February 1–14, 2026, include:
February 1: Shinwa Co Ltd (civil engineering/construction) and Hosowaka Micron Group (industrial machinery manufacturing) both claimed by Everest; no specified data sizes, but operational disruptions implied, with 42 GB exposed including databases and internal documents.
February 2: KOUEI (manufacturing/supply) claimed by Qilin; exfiltration details unavailable, focusing on alloy materials data.
February 5: AOT Japan Ltd (logistics/freight) claimed by INC Ransom; tied to a confirmed data breach exposing customer and operational info, leak size unknown.
February 2: C**U*O Co., Ltd claimed by Nightspire; estimated attack date February 5, internal data unavailable.
February 14: Makimura Co., Ltd. claimed by Nightspire; estimated attack date January 31 (impacts into February), including internal data, financials, and client lists.
Attacks often leveraged supply chain weaknesses, with a 30% noted increase in Japan-targeted ransomware per industry reports. Victims reported extended downtimes, highlighting vendor risks.
📊 Data Breaches in Japan
Standalone breaches beyond ransomware affected personal and corporate data, impacting over 150,000 records in healthcare, aviation, retail, and logistics. Key incidents:
February 11: Japan Airlines baggage delivery system breach exposed data of 28,000 users, including names, emails, phone numbers, flight details, and hotel destinations; unauthorized access confirmed, no exploitation reported.
February 13: Tenga (consumer goods/sex toys) suffered a hacker intrusion into employee inboxes, stealing customer names, emails, and correspondence; scale estimated at thousands, with privacy risks amplified.
Broader trends: Aon survey (February 12) ranks cyber attacks/data breaches as Japan's top business risk for 83% of firms. S&P Global (February 4) highlights growing corporate vulnerability post-breaches. Public perception survey (February 12) shows 79.7% feel safety worsened due to data breaches and fraud. Government breaches spanned Asia-Pacific, including Japan in multi-nation leaks.
⚔️ APT/Threat Campaigns Targeting Japan
State-aligned campaigns intensified, with Chinese and North Korean actors prioritizing espionage amid regional tensions. Notable activities:
Ongoing (noted February 2026): China-linked Bronze Butler (Tick) exploited Lanscope Endpoint Manager zero-day (CVE-2025-61932) for root access in Japanese businesses, backdooring networks since mid-2025.
Ongoing (referenced February 2026): APT-C-60 (South Korea-aligned) deployed updated SpyGlace malware in espionage against Japanese organizations, using WPS Office zero-days and GitHub for distribution.
Ongoing: Chinese APTs (e.g., Salt Typhoon, Volt Typhoon, Silk Typhoon) targeted critical infrastructure and telecom, part of sustained 2021-2026 campaigns for long-term access.
February 9: Amaranth-Dragon (linked to APT41) used CVE-2025-8088 in phishing against Japanese government/law enforcement, deploying Telegram-based RAT.
Ongoing: Earth Baxia (China) exploited GeoServer (CVE-2024-36401) against APAC, including Japanese military.
Ongoing: Seven Chinese APT groups coordinated espionage on Japan/ASEAN, abusing vulnerabilities for data theft.
TTPs involve zero-day exploits, social engineering, and supply chain compromises, tied to Taiwan/South China Sea tensions.
🛡️ Recent 0-day/N-day Exploits Affecting Japan
Exploits patched in February targeted critical systems, with Japanese firms in tech/energy vulnerable:
February 10: Microsoft Patch Tuesday fixed 59 CVEs, including six zero-days exploited in wild (e.g., CVE-2026-21510 Windows Shell bypass, CVE-2026-21513 MSHTML, CVE-2026-21514 Word, CVE-2026-21519 Desktop Window Manager EoP, CVE-2026-21533 Remote Desktop EoP, CVE-2026-21525 DoS); active attacks on Japanese orgs via malicious links/files/Office docs.
Ongoing: Bronze Butler exploited Lanscope zero-day (CVE-2025-61932) for root in Japan; patched but residual risks.
January Pwn2Own Automotive exposed 76 zero-days in EV/IVI systems (e.g., Tesla), with ongoing implications for Japan's auto sector.
Events like JSAC2026 emphasized Ivanti-like vulns; automotive/tech sectors at high risk.
📈 Security Recommendations & Mitigations
Japanese entities face heightened risks, with cyber threats topping concerns (83%). Trending TTPs: AI-generated malware (Amaranth-Dragon, Kimsuky), supply chain attacks (Qilin, Everest), zero-day exploitation (Bronze Butler), and Group Policy abuse (Chinese APTs). Defensive postures: Implement Japan's Active Cyber Defense Law (effective 2026) for proactive monitoring. Recommendations include rapid patch management (e.g., Microsoft zero-days), AI-based threat detection, multi-factor authentication for vendors, zero-trust architectures, and endpoint monitoring. Monitor darkweb for leaks; conduct supply chain audits to mitigate third-party risks.
🔮 Forward-Looking Analysis and what to stay alert?
Ahead, anticipate 40%+ ransomware spike via AI/cloud zero-days (e.g., Qilin evolutions), with Nightspire/INC targeting manufacturing. APT intensification from China (Bronze Butler, APT-C-60) and North Korea amid Taiwan tensions, focusing critical infrastructure/telecom. Emerging: AI-driven autonomous campaigns (polymorphic malware, extortion bots), hybrid espionage/crime (Salt Typhoon-style). Stay alert for supply chain pivots, darkweb sales surges, geopolitical triggers like elections, and new zero-days in Office/Windows. Proactive: Leverage new laws for active defense, darkweb monitoring, and zero-trust to counter 2026 escalations.













