top of page

Media Coverage


A copy of the fake installer incident that occurred even when downloaded from the official website
An incident has been identified where users faced potential risk from software installers distributed via official websites.
The key takeaway is that even official downloads are not always risk-free.
Modified links, altered distribution paths, or fake installers can lead to unintended compromise.
This article highlights what users should verify and what website operators should review, without assuming that “official” automatically means “safe.”
2 days ago

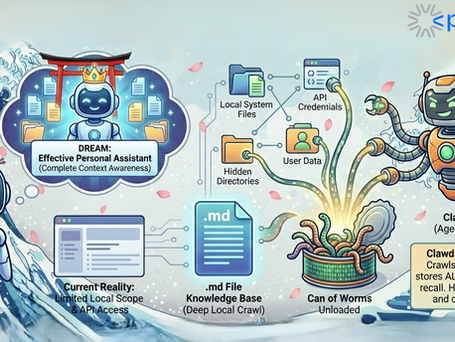
Oh Clawp! A 1-Click ClawdBot Exploit leads to RCE over GatewayUrl exfiltrating single-layer authentication Token & Typosquatting campaigns
Authors: Reyben T. Cortes, Azim Uddin, Abdullah Mamun, ThreatCluster , DefusedCyber Happy Monday! Unless you've been living under a rock, we're tracking the development of one of the most controversial conversations in the security community regarding the release of ClawdBot, that is what we will only call it for today. While this isn't the first iteration, this agentic tool unloads a can of worms into your local system by crawling every single crevice of files and API crede
2 days ago


Cyber diagnosticians in white coats appear | NCA Exhibition Report
PIPELINE exhibited at the NCA Annual Conference with the concept of “cyber diagnosticians in white coats.”
This report introduces the booth experience, visitor reactions, and our approach to making cybersecurity approachable.
6 days ago


Ransomware Risks Facing India in 2025: A Strategic Analysis by Unit Zero
Author: MD. Azim Uddin Figure 1: India's Cyber Digital Monsoon 2025 As we monitor the movements of threat actors across the Asia Pacific (APAC) region, examining attack trends and the evolution of cyber warfare from low-skill attacks conducted by inexperienced actors to advanced state-sponsored operations, it is clear that 2025 marked a sobering moment for India’s cybersecurity landscape. Our analysis presents a concerning reality: India has become one of the world's top targ
Jan 20


CVE-2025-68613: Nye8! - APAC Groups Exploit PoC & Four CVSS10 Critical n8n Vulnerabilities leads to Remote Code Execution
Author(s): Reyben T. Cortes, Azim Udin, Unit Zero Threat Research Team, DefusedCyber Figure 1: Pie chart statistics of top n8n versions in Japan Happy New Year! Since early December leading up to the Holiday break we flagged a series of n8n vulnerabilities that came to our immediate attention, for a good reason. N8n one of the most trending, Free-to-start low-code no code automation platform used by all types of users and organizations worldwide. Due to it's extremely scalabl
Jan 14


React2Shell Timeline: Bypass that WAF! Analyzing the Exploit Payload & Implications to Japan's Digital Infrastructure
Author(s): Reyben T. Cortes Happy Friday! It was the calm before the storm, within the past 48 hours the security community finally came full circle after details of a working PoC (Proof of Concept) exploit recently went public for CVE-2025-66478, an unpublished Next.js vulnerability built on React created by Vercel. With Its focus on making beautiful interactive user interface, the widely used frontend library garnered over 82 million websites worldwide, becoming the world's
Dec 10, 2025

Visible risks, assets to protect
With real-time data, dark web intelligence, and expert response, we identify threats before they strike and protect your critical assets.
bottom of page