In 2023, a staggering 72.7% of organizations worldwide experienced a ransomware attack. Data is as valuable as currency and the threat landscape is constantly evolving, and it’s crucial to understand why your business needs tailored cybersecurity protection now more than ever.
Managed cyber security has become a critical shield for businesses worldwide. With cyber-attacks becoming more sophisticated and frequent, the question is no longer if your business will be targeted, but when.
Let’s dive into the essence of managed cyber security, its importance, and the key indicators that resonate with businesses seeking to fortify their cyber defenses.
What is Managed Cyber Security and Why Businesses Need It
Managed Cyber Security Services (MSS) refers to the outsourcing of monitoring and management of security devices and systems. Common services include managed firewalls, intrusion detection, virtual private networks, vulnerability scanning, and anti-viral services.
With the increasing complexity and volume of threats in the cyber environment, having a dedicated team to monitor, assess, and react to threats can be the difference between a secure business operation and a disastrous data breach.
The Role of Managed Cyber Security in Preventing Ransomware Attacks and Data Breaches
Ransomware attacks and data breaches have become alarmingly common, causing significant financial and reputational damage to affected businesses.
Managed cyber security plays a pivotal role in defending against such threats by employing advanced threat detection mechanisms, conducting regular vulnerability assessments, and implementing robust data protection strategies.
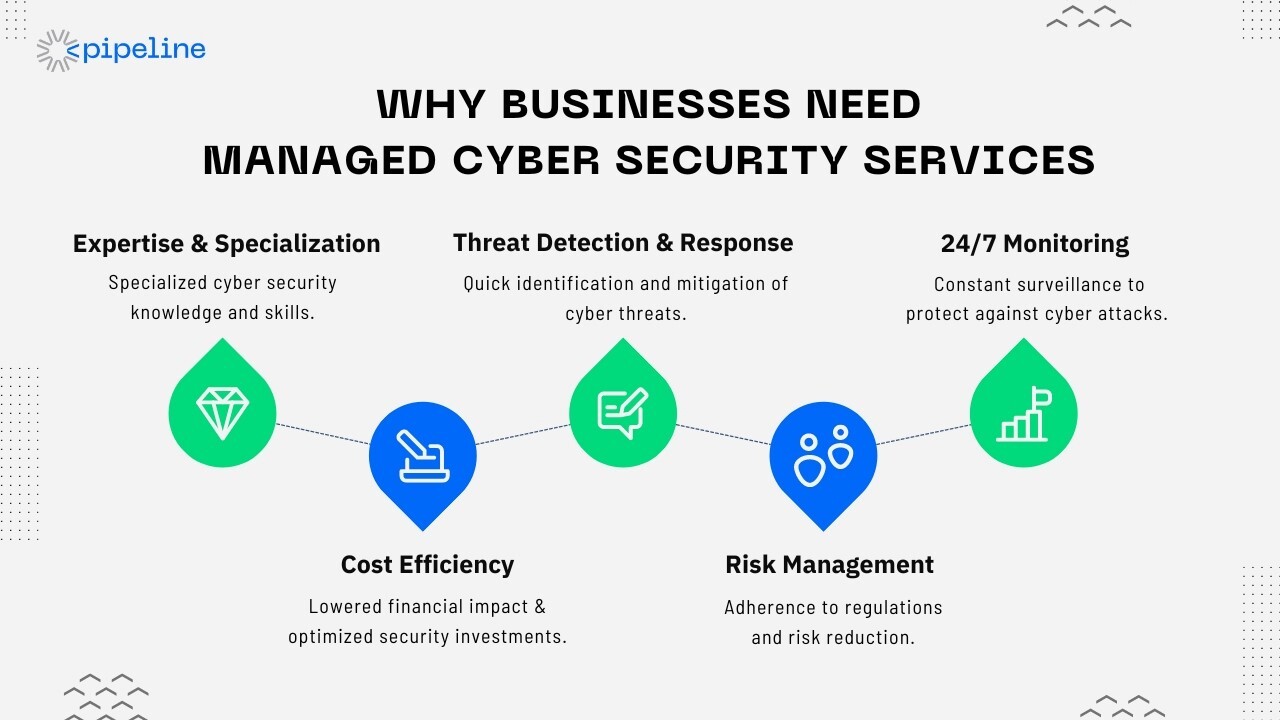
Signs Your Business Requires Managed Cyber Security Services
Recognizing the signs that your business requires managed cyber security services is crucial for timely intervention.
Key indicators include:
- Frequent security breaches or attempted attacks.
- Lack of in-house cyber security expertise.
- Insufficient cyber security measures compared to industry standards.
- Regulatory compliance requirements.
- The need for 24/7 security monitoring.
Cost-Benefit Analysis of Investing in Managed Cyber Security
With 300,000 systems vulnerable to new loop DoS attacks, it is essential to invest in managed cyber security services. Investing in managed cyber security services involves analyzing the potential costs of cyber threats against the expenses of engaging a managed services provider.
For many businesses, the cost of a data breach far exceeds the investment in preventative managed security services, making it a financially sound decision.
Managed Cyber Security Solutions for Small to Medium Businesses
Approximately 73% of small business owners around the world experienced a cyber-attack last year, with data breaches primarily targeting employee and customer information. Small to medium businesses (SMBs) are often more vulnerable to cyber-attacks due to limited resources and expertise.
Managed cyber security solutions offer a tailored approach to security, allowing SMBs to benefit from high-level protection without the need for extensive in-house capabilities.
Integrating Managed Cyber Security into Your Existing IT Infrastructure
Integrating managed cyber security services with existing IT infrastructure requires careful planning and communication. Providers typically offer seamless integration options that minimize disruption and ensure continuous protection across all systems and devices.
Elevating Network Security: The First Line of Defense Against Cyber Threats
The importance of robust network security cannot be overstated. As hackers become increasingly sophisticated, the need for robust network security alongside an advanced security solution that can effectively shield your network from unauthorized access and cyber-attacks becomes paramount.
Network security serves as the foundation of your enterprise's defense mechanism, safeguarding critical information and maintaining the integrity of your data-security measures.
- Implementing Advanced Security Controls: Deploy intrusion prevention systems, utilize virtualization for secure environments, and integrate security intelligence tools to identify threats early.
- Strengthening Perimeter Defense: Leverage firewalls, VPNs, and advanced persistent threat (APT) detection to create a formidable barrier against attackers.
- Regular Vulnerability Management: Conduct penetration testing and vulnerability assessments to identify and remediate weaknesses in your network security posture.
It's crucial to recognize that investing in state-of-the-art network security solutions and adopting proactive security policies are essential steps in protecting your organization from the evolving landscape of cyber threats.
Choosing the Right Managed Cyber Security Provider
Selecting the right provider is crucial. Businesses should look for providers with a strong track record, industry-recognized certifications, and the ability to offer customized solutions that align with their specific needs and challenges.
Managed Cyber Security Versus Traditional IT Security Measures
Managed cyber security services offer several advantages over traditional IT security measures, including access to specialized expertise, advanced technology solutions, and the ability to scale services as needed. This comprehensive approach ensures businesses are equipped to face current and emerging cyber threats, including protection against ransomware.
The Impact of Managed Cyber Security on Business Continuity Planning
Incorporating managed cyber security into business continuity planning ensures that businesses can maintain operations in the face of cyber incidents. This comprehensive approach to risk management is critical for minimizing downtime and financial losses during and after an attack.
The Future of Managed Cyber Security Services for Businesses
The future of managed cyber security services is likely to see increased adoption of AI and machine learning technologies, further enhancing the ability to detect and respond to threats in real-time. As cyber threats continue to evolve, so will the solutions designed to combat them, ensuring businesses can navigate the digital landscape with confidence.
The Importance of Managed Cyber Security in Remote Work Environments
Even bigger corporates like Apple, are now facing encryption and data threats. The shift towards remote work has exacerbated the cyber security challenges businesses face. Remote environments often lack the robust security measures found in traditional office settings, making them prime targets for cybercriminals.
Managed cyber security services extend protective measures to remote workforces, implementing end-to-end encryption, secure VPN services, and multi-factor authentication to safeguard data irrespective of where employees are working. This not only enhances security but also supports the flexibility that modern workforces demand.
Customized vs. Out-of-the-Box Managed Cyber Security Solutions
Every business is unique, with specific risks, compliance requirements, and security needs. While out-of-the-box solutions can provide a basic level of protection, customized managed cyber security solutions offer a tailored approach that aligns with the specific needs and risk profile of your business. Check out our CSaaS guide to know more.
Customization can range from specialized threat intelligence services to bespoke security policy development, ensuring that your business is not just secure, but also compliant with industry regulations and standards.
Managed Cyber Security Compliance and Regulatory Requirements
Navigating the complex landscape of cyber security compliance and regulatory requirements is a formidable challenge for many businesses. Managed cyber security services not only ensure that your business's defenses are robust but also that they are in strict adherence to relevant data protection laws, industry regulations, and security standards.
Whether it's GDPR, HIPAA, or PCI DSS, a managed service provider can help ensure that your business is not only protected against cyber threats but also against legal and financial repercussions associated with non-compliance.
The Role of AI and Machine Learning in Managed Cyber Security
Artificial Intelligence (AI) and Machine Learning (ML) are at the forefront of the evolution of managed cyber security services. These technologies enhance the ability of security systems to learn from past incidents, predict potential threats, and respond to them with minimal human intervention.
The incorporation of AI and ML into managed cyber security offerings represents a leap forward in proactive threat detection, from phishing protection and malware defense to advanced threat protection and security analytics. The newest news shows that StrelaStealer phishing attacks have affected over a hundred businesses in the E.U. and U.S.
Evaluating the ROI of Managed Cyber Security Investments
Understanding the return on investment (ROI) of managed cyber security is critical for businesses. The evaluation encompasses not just the cost savings from prevented security incidents but also the value of maintaining customer trust, protecting intellectual property, and ensuring business continuity.
Managed cyber security services can significantly reduce the budgetary impact of cyber threats, including direct costs like ransom payments and indirect costs such as downtime, legal fees, and reputational damage.
Mitigating Vulnerabilities: A Strategic Approach to Strengthening Information Security
Vulnerabilities in an organization's information-security framework can serve as open doors for malicious actors looking to exploit data for nefarious purposes.
The path to robust enterprise security lies not only in identifying these weaknesses but also in implementing a comprehensive vulnerability management program that includes both prevention and remediation strategies.
- Prioritizing Security Awareness: Educate employees through security training programs about social-engineering attacks, phishing frauds, and best practices for email security.
- Deploying Endpoint Protection: Utilize cloud-based antivirus and anti-malware solutions for malware protection, ensuring all endpoints are secured against viruses and spyware.
- Enhancing Application Security: Apply rigorous security measures in web-application development and deployment, including regular security audits and testing for vulnerabilities.
A dynamic approach to vulnerability management—encompassing both technological solutions and human elements of security—can significantly reduce security risks and enhance your organization's overall defense strategy.
Transitioning from In-House IT to Managed Cyber Security Services
For many businesses, the transition from in-house IT security measures to a managed service provider represents a strategic shift towards more comprehensive, advanced security solutions.
This transition involves a detailed assessment of current security posture, identification of gaps, and a clear understanding of business objectives. Managed service providers can offer the expertise, tools, and technologies required to elevate your cyber security measures, providing peace of mind and allowing your in-house team to focus on core business activities.
The Top Managed Cyber Security Threats Businesses Face in 2024
Forecasts by Cybersecurity Ventures suggest that by 2031, the annual financial toll of ransomware could soar to approximately $265 billion USD, a dramatic increase from $20 billion in 2021.
Understanding the evolving cyber threat landscape is crucial as we look towards the future. In 2024, businesses are expected to face various sophisticated threats, including ransomware attacks, phishing schemes, insider threats, and state-sponsored cyber-attacks.
Managed cyber security services equip businesses to confront these challenges head-on, leveraging cutting-edge security technologies, threat intelligence, and incident response strategies to mitigate risks and protect critical assets.
Best Practices in Managed Cyber Security for E-commerce Platforms
E-commerce platforms, with their vast amounts of transaction data and customer information, are particularly vulnerable to cyber-attacks. Implementing best practices in managed cyber security, such as secure transaction processing, robust encryption, and continuous security monitoring, is essential for protecting against data breaches, ensuring PCI DSS compliance, and maintaining customer trust.
Managed service providers specializing in e-commerce can offer customized solutions that address the unique challenges of the online retail environment.
Integrating Managed Cyber Security into Your Business Strategy
Integrating managed cyber security into your overall business strategy involves aligning security measures with business objectives and ensuring that cyber security investments are strategic and contribute to long-term business growth.
Whether it is through securing emerging technologies, enabling digital transformation, or enhancing customer trust, managed cyber security is a foundational element of a forward-looking business strategy.
Cultivating a Culture of Security: From People to Processes
The bedrock of effective security management is not just advanced security technology; it's also about fostering a culture of security awareness and compliance throughout the organization.
This integrated approach to security encompasses everything from access management and data loss prevention to the development of comprehensive security policies that guide the behavior of all stakeholders.
- Implementing Comprehensive Security Policies: Develop and enforce clear security policies that cover all aspects of your organization's operations, from cloud security to mobile security.
- Advancing Security Operations with SIEM: Use Security Information and Event Management (SIEM) tools to provide centralized logging and real-time analysis of security alerts generated by applications and network hardware.
- Promoting Continuous Security Training: Engage employees in ongoing security training and awareness programs to recognize and respond to security threats promptly.
By integrating security into the DNA of your business processes and ensuring that every employee is equipped with the knowledge and tools to contribute to the security posture, businesses can significantly mitigate the risk of a security breach and protect their critical infrastructure against the ever-present threat of cybercrime.
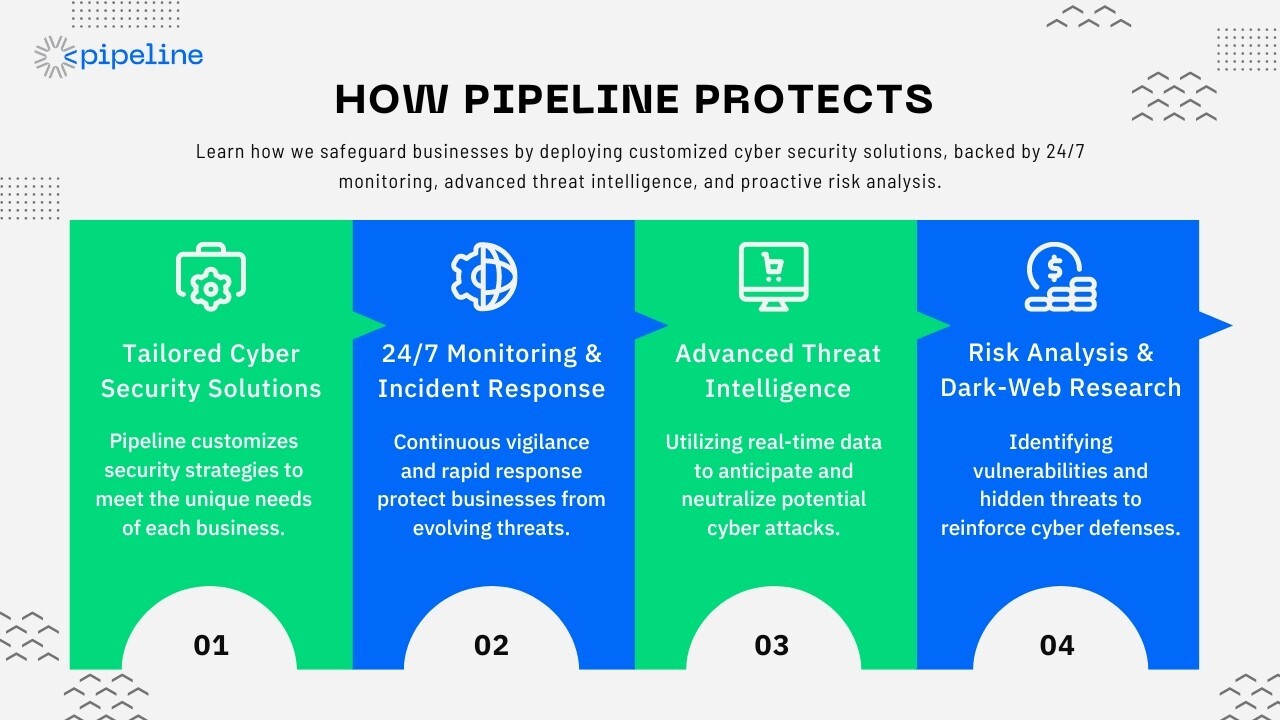
How Pipeline Protects: Your Digital Security Partner
Now that cyber threats parallel digital advancements, Pipeline emerges as a vigilant protector, offering a robust array of cyber security services tailored to the diverse needs of businesses.
Our expertise shines in deploying advanced log analytics, securing emails against phishing, safeguarding internet access with a secure gateway, and managing endpoint security with precision.
Coupled with our real-time threat intelligence, Pipeline's solutions are designed not just to respond but to anticipate and neutralize threats, ensuring your data's safety globally. Our 24/7 team specializes in customized incident responses, and risk analysis consulting, and even delves into dark web research to pre-empt potential cyber-attacks, reinforcing your defenses and keeping your operations resilient.
Why Partner with Pipeline?
Choosing Pipeline as your cybersecurity ally means entrusting your digital safety to experts who grasp the intricacies of cyber threats and the importance of robust protection in today's digital age.
Our commitment to your business's security is unwavering, with round-the-clock support and a suite of adaptable, innovative solutions that secure your operations. For resources and use cases, check our Resource Center for more.

By integrating Pipeline's cybersecurity strategies into your business framework, you ensure not only the protection of your digital assets but also the freedom to innovate and expand, unhampered by the shadows of cyber threats. Let Pipeline guard your digital frontier, ensuring a safe, resilient future for your business, its employees, and customers in the ever-evolving digital world.