In the dynamic landscape of cybersecurity, staying ahead of evolving threats is paramount.
For CISOs, Head of ITs, and IT Administrators, the choice of a cybersecurity partner is a strategic decision that can shape the security posture of an organization. In this realm of digital defense, Censys Search stands out as a beacon of innovation and reliability.

Understanding Censys Search
Censys Search is not just another cybersecurity company; it's a strategic ally in the battle against cyber threats. With a commitment to excellence, Censys Search brings forth a range of cutting-edge solutions designed to fortify your digital infrastructure.
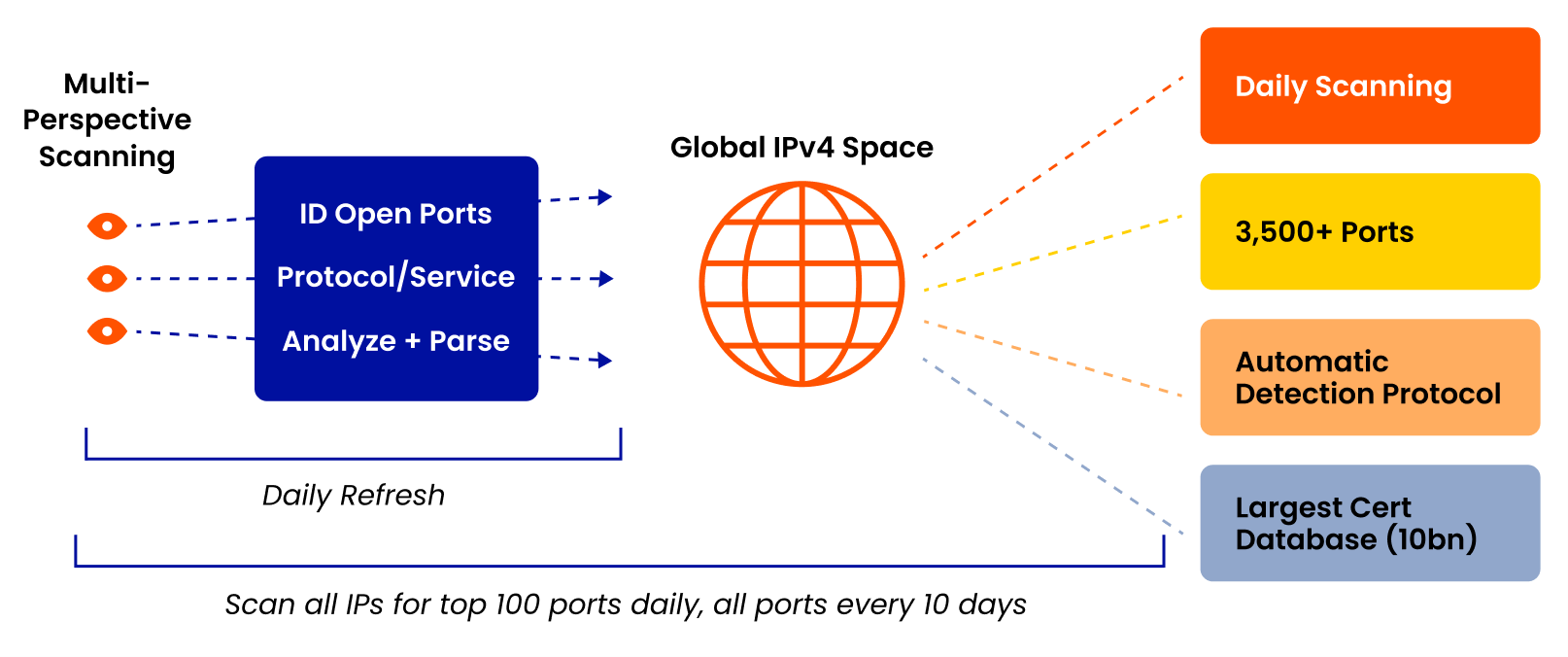
Key Features and Solutions
Explore the arsenal of cybersecurity excellence as Censys Search unveils key features and solutions designed to fortify your digital defenses against evolving threats.
Threat Intelligence Mastery
Censys Search empowers organizations with unparalleled threat intelligence. The platform sifts through vast data sets, providing real-time insights into emerging threats. This proactive approach enables security teams to stay a step ahead and fortify defenses effectively.
Incident Response Excellence
Rapid response is crucial in the face of a cyber incident. Censys Search's incident response solutions are crafted with precision, ensuring swift and effective mitigation of threats. This not only minimizes potential damage but also aids in learning from each incident for future resilience.
Advanced Analytics for Informed Decision-Making
In the world of cybersecurity, informed decisions are the bedrock of success. Censys Search leverages advanced analytics to provide actionable intelligence. CISOs and IT leaders gain a comprehensive understanding of their digital environment, enabling strategic decisions to mitigate risks effectively.
Why Choose Censys Search
Discover the compelling reasons why Censys Search stands out as the strategic choice for CISOs, Head of ITs, and IT Administrators seeking unparalleled cybersecurity resilience and innovation.
Proven Track Record
Censys Search boasts a proven track record of safeguarding organizations across diverse industries. From finance to healthcare, its solutions have consistently demonstrated effectiveness in the face of sophisticated cyber threats.
User-Friendly Interface
Cybersecurity shouldn't be complicated. Censys Search understands this and offers an intuitive, user-friendly interface. This simplicity ensures that your security teams can leverage the full power of the platform without unnecessary complexity.
Scalability and Adaptability
As your organization evolves, so do cyber threats. Censys Search provides scalable solutions that can adapt to the changing dynamics of your digital landscape. This scalability ensures that your cybersecurity strategy remains robust and future-proof.
How Censys Search Works
Understanding the inner workings of a cybersecurity solution is crucial for CISOs, Heads of IT, and IT Administrators evaluating potential partners. Censys Search's approach is rooted in sophistication and efficiency, providing a comprehensive understanding of its operational mechanisms.
1. Data Aggregation and Correlation
Censys Search begins by aggregating vast amounts of data from diverse sources, both internal and external. This data includes network logs, endpoint activities, threat feeds, and more. Through advanced correlation techniques, the platform identifies patterns and anomalies that could signify potential threats.
2. Threat Intelligence Integration
The heart of Censys Search lies in its integration of real-time threat intelligence. By continuously monitoring global threat landscapes, the platform ensures that your organization is shielded against the latest and most sophisticated cyber threats. This proactive approach is instrumental in preventing attacks before they can exploit vulnerabilities.
3. Machine Learning and Behavioral Analysis
Leveraging the power of machine learning and behavioral analysis, Censys Search goes beyond traditional rule-based approaches. The platform learns and adapts to the unique digital fingerprint of your organization, identifying deviations from normal behavior. This proactive stance is essential in detecting novel and previously unseen threats.
4. Actionable Insights and Reporting
Censys Search doesn't just stop at detection; it excels in providing actionable insights. The platform generates clear and concise reports, highlighting potential risks, ongoing incidents, and recommended mitigation strategies. This empowers security teams to make informed decisions promptly.
5. Incident Response Orchestration
In the event of a security incident, Censys Search shines in its incident response orchestration. Automated workflows streamline the response process, ensuring that threats are contained and eradicated swiftly. This orchestrated response not only minimizes downtime but also contributes to a continuous cycle of improvement in your organization's security posture.
6. Continuous Monitoring and Adaptation
Censys Search is not a static solution. It operates on the principle of continuous improvement. The platform constantly evolves, learning from new threats and adapting its algorithms to changing landscapes. This ensures that your organization remains resilient in the face of emerging cybersecurity challenges.
In Summary, Censys Search's operational methodology is a symphony of data intelligence, advanced analytics, and proactive defense. By understanding how Censys Search works with CISOs, Heads of IT, and IT Administrators gain insight into the robust mechanisms that form the foundation of this cybersecurity powerhouse.
Use Cases of Censys Search
Investigate Compromise Indicators
When it comes to threat hunting, Censys' extensive, fully indexed datasets help you identify the needles in the haystacks. You can use Censys to build, validate, and examine IoCs on hosts all across the Internet using threat intelligence from internal or public sources.
You'll need a solid understanding of the Censys host fields where the indicators you're looking for are placed, so make use of the Host and Certificate schemas.
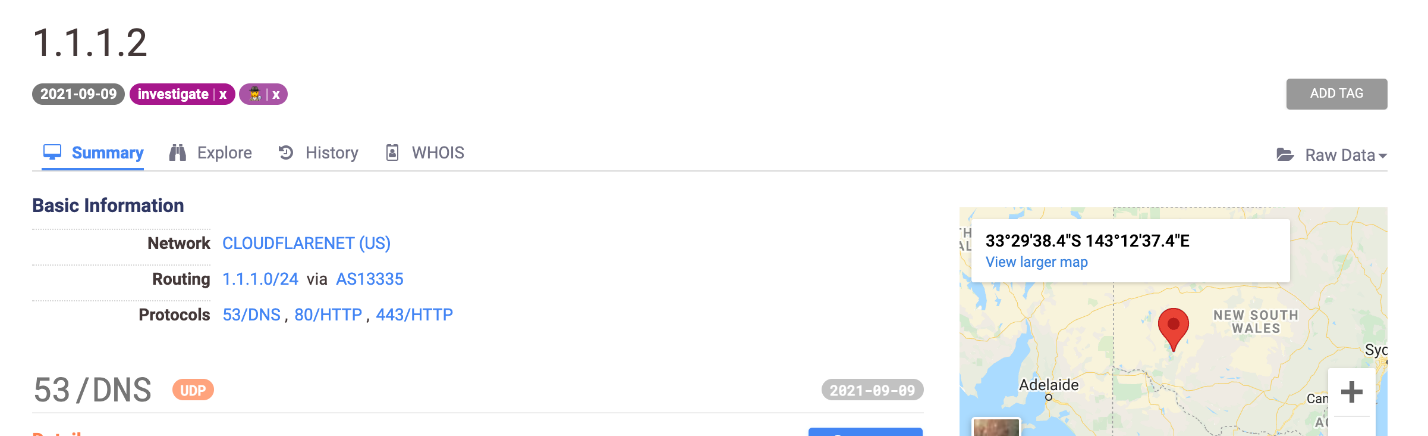
Adding Host and Certificate Data to Internal Threat Feeds
You can search for IP addresses that your hosts are connecting to or receiving connections from as you monitor network activity. The Search 2.0 view host endpoint is fast and efficient, allowing you to immediately supplement your network security logs with Censys host profiles.
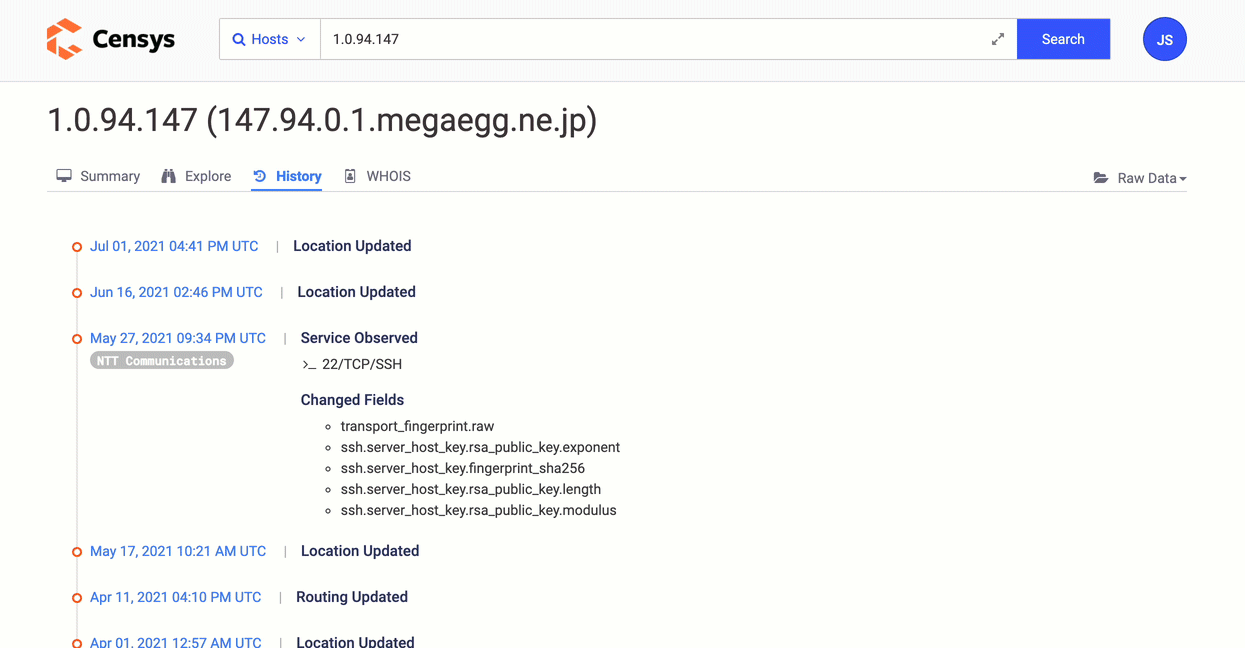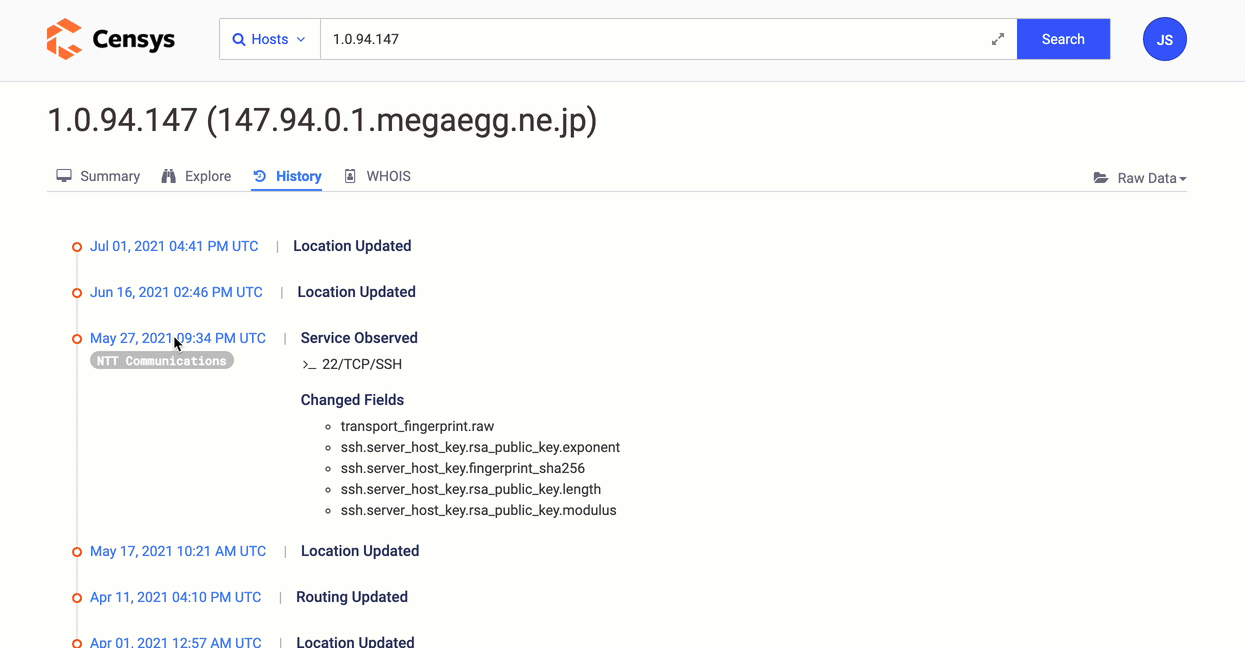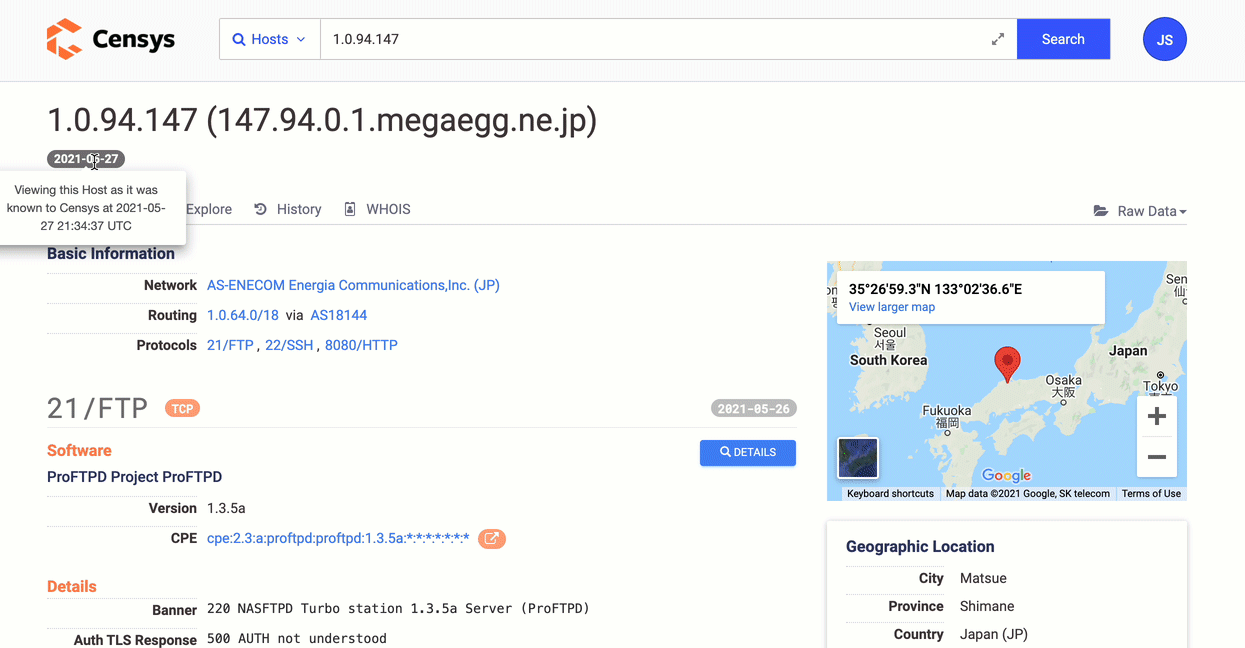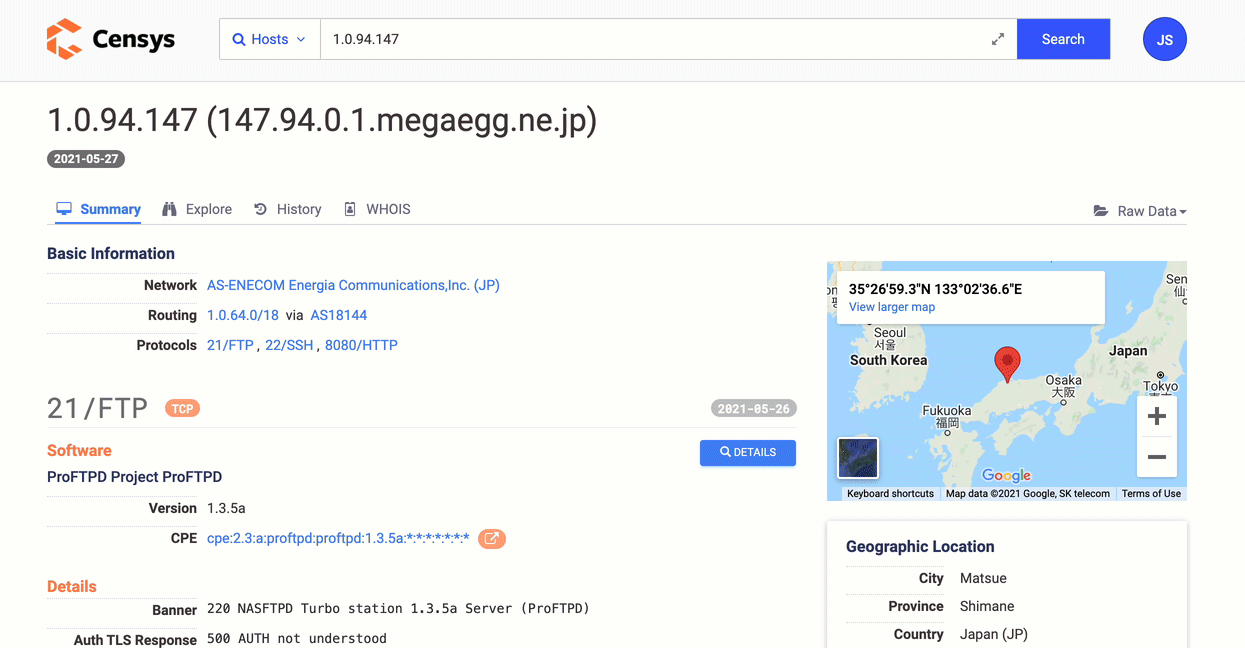
Create an Adversary Infrastructure Timeline
Look at how a host has evolved over time. Examine how services appeared and departed, as well as how fresh certificates were offered, to determine how this infrastructure was exploited.
Map An External Attack Surface
Analyze your company's Internet presence from the outside. Profile hosts, services, and certificates to evaluate your overall security posture and make adjustments such as decreasing public exposure, fixing obsolete or vulnerable systems, and implementing proper Internet asset hygiene.

Conclusion
In the relentless pursuit of cybersecurity excellence, choosing the right partner is non-negotiable. Censys Search emerges as a beacon of trust, offering a comprehensive suite of solutions that empower CISOs, Heads of IT, and IT Administrators to navigate the complex landscape of cyber threats with confidence.
Safeguard your digital assets, elevate your cybersecurity strategy – choose Censys Search.









