Our digital landscape is continuously evolving, and so is the surge in cyberattacks. Cybersecurity Ventures forecasts global cybercrime costs will rise 15% yearly, hitting $10.5 trillion annually by 2025.
From phishing to ransomware, these cyberattacks pose an unprecedented threat to businesses of all sizes. The cybersecurity climate is more volatile than ever, with SMBs and large enterprises alike grappling with the complexities of safeguarding their digital assets.
The heightened cybersecurity climate underscores the critical need for robust and adaptable defense mechanisms. Enter Cybersecurity-as-a-Service (CSaaS), a modern solution designed to offer businesses comprehensive cybersecurity support, addressing the intricate challenges of protecting digital assets in a volatile cyber environment.
What Exactly is Cybersecurity-as-a-Service?
At its core, Cybersecurity-as-a-Service (CSaaS) is a model where cybersecurity management and operations are outsourced to a dedicated team of experts. This service encompasses a wide array of security measures, including but not limited to vulnerability assessments, penetration testing, and compliance assistance.
CSaaS is designed to provide businesses with 24/7 cybersecurity coverage, using the domain ability in cybersecurity of seasoned professionals to protect against cybercrime effectively.
Through CSaaS, organizations gain access to top-tier security infrastructure without the hefty investment in in-house resources.
What Has Led to the Rise of CSaaS?
In the last few years, several key factors have contributed to the increase in CSaaS. Some notable ones are:
· Digital Expansion
· Cybersecurity Skills Gap
· Cost-Effectiveness
Let us explain. Firstly, the increasing sophistication of cyberattacks and the expansion of attack surfaces, thanks to the proliferation of IoT (Internet of Things) and cloud services, have made traditional security measures obsolete.
Secondly, digital business transformation has accelerated cloud migration, underscoring the need for cloud-based security solutions that can dynamically adapt to the changing digital environment.
Furthermore, the scarcity of cyber security experts has made it challenging for companies, especially SMBs, to recruit and retain in-house talent for cybersecurity management. CSaaS is a cost-effective solution that provides small and medium businesses access to cybersecurity experts and advanced technologies like AI in cybersecurity and automation in threat response.
How Does CSaaS Differ from Traditional Cybersecurity Solutions?
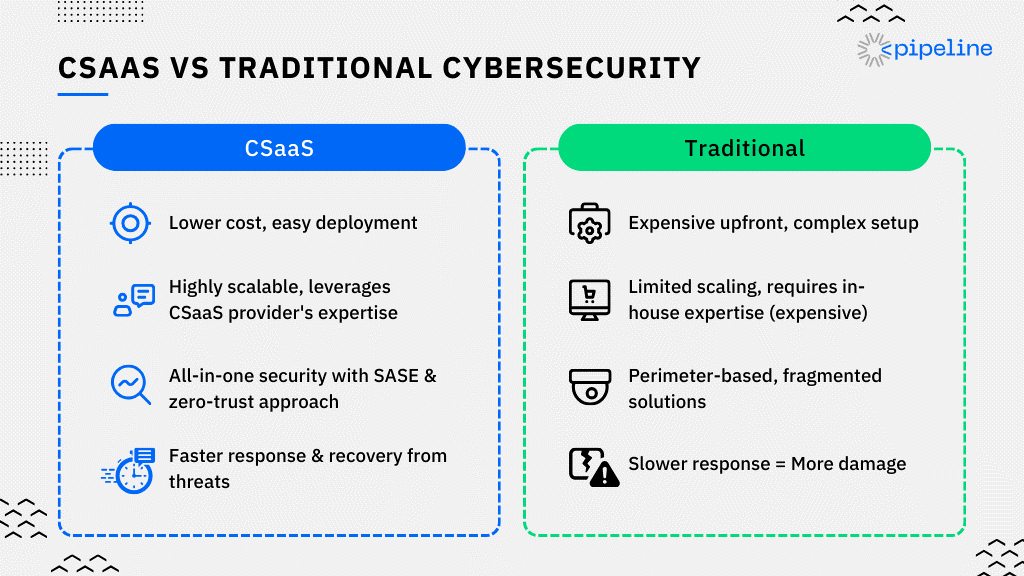
Unlike traditional cybersecurity solutions, CSaaS (Cybersecurity as a Service) runs on a subscription-based model. It drops the need for significant upfront investments in hardware and software. Organizations don't have to bear the ongoing costs of training and keeping an in-house cybersecurity team.
This subscription model democratizes access to enterprise-grade cybersecurity cloud infrastructure. It ensures scalability and flexibility to meet an organization's evolving security needs. CSaaS providers use the Security Operations Center (SOC) to offer managed detection and response (MDR) services. This provides real-time visibility into threats and enables proactive mitigation measures.
CSaaS integrates seamlessly with existing IT environments, providing a unified security posture. It includes endpoint protection, data encryption and backup, and compliance assistance.
This comprehensive coverage, combined with the shift towards SASE (Secure Access Service Edge) architecture and zero trust security, marks a significant departure from traditional perimeter-based, reactive cybersecurity approaches.
Finally, we need to understand speed is key in cybersecurity! Every minute a business is down due to a cyberattack translates to lost revenue. This can damage brand reputation and cause significant financial losses.
For instance, one of our customers in Bangladesh lost a staggering $600,000 in sales due to being down for only one day (That’s $416.66 lost every single minute).
What Services Are Included in CSaaS?
CSaaS is a full-spectrum cybersecurity service offering that includes everything a business needs to stay digitally secure. This includes:
· Cybersecurity Consultation: Tailored advice to fortify your digital defenses.
· Vulnerability Assessments: Finding weak spots in your network security.
· Penetration Testing: Ethical hacking to test the resilience of your systems.
· 24/7 Cybersecurity Coverage: Constant monitoring for any signs of a data breach.
· Managed Detection & Response (MDR): A crucial element that provides proactive surveillance and rapid response to mitigate threats and intrusions.
· Cybersecurity Compliance Assistance: Ensuring your business meets all regulatory and legal cybersecurity standards.
· Endpoint Protection: Securing every endpoint, from servers to mobile devicres, against cyber-attacks.
· Data Protection, Encryption and Backup: Protecting your data, both at rest and in motion.
By using cloud technologies, CSaaS delivers these services in a model that ensures businesses have access to innovative cybersecurity measures without the heavy lifting of managing them in-house.
How Does Managed Detection and Response Fit into CSaaS?
Managed Detection and Response (MDR) is the heartbeat of CSaaS, pumping proactive, real-time threat detection and response capabilities throughout a business's cybersecurity infrastructure.
Unlike traditional security measures that react after an attack has occurred, MDR takes a proactive stance. It employs advanced AI in cybersecurity and automation in threat response to find potential threats before they manifest into full-blown cyberattacks.
As a result of the early detection mechanism, businesses can neutralize threats and minimize potential damage. MDR transforms CSaaS from a passive shield into an active, dynamic guardian.
The Core Advantages of CSaaS
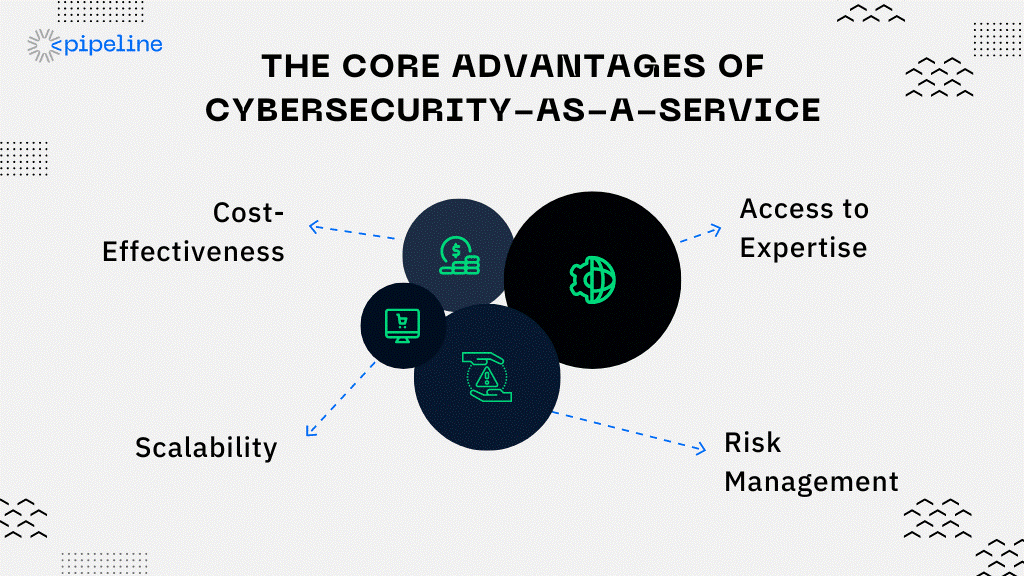
Cost-Effectiveness
CSaaS operates on a model that cuts hefty upfront investments by spreading out expenses over time, making cyber security services more accessible, especially for small and medium-sized businesses (SMBs).
You don’t have to go out and make in-house teams filled with experts anymore. Our Cybersecurity-as-a-Service (CSaaS) model offers a virtual CISO on demand, offering top-tier ability at a fraction of the cost of building an in-house cybersecurity team.
Access to Expertise
Businesses gain direct access to a pool of cybersecurity experts without the daunting task of recruiting and keeping talent and benefit from the latest security technologies and practices.
Scalability
CSaaS providers can tailor their offerings, ensuring businesses are never over or under-protected, whether it's expanding cloud services or integrating new IoT devices. These security providers can go from making budget packages for smaller businesses to total enterprise security.
Risk Management
CSaaS goes beyond mere defense, offering comprehensive security risk assessments, cybersecurity policy development, real-time threat monitoring, and the robust capabilities of a Security Operations Center (SOC) to minimize risk exposure.
Choosing the Right CSaaS Provider
When it’s time to pick a cyber security service provider, think of it like choosing a new smartphone. You want the best features, but you also need something that fits your lifestyle (or, in this case, your business). Here's the breakdown:
· Expertise: This is non-negotiable. Your provider should be like the cybersecurity Yoda, wise beyond measure in the ways of cyber security service offerings, from thwarting DDoS attacks to managing compliance with grace.
· Technology: Look for the latest and greatest. We're talking cutting-edge cloud technologies, AI in cybersecurity for smarter threat detection, and robust systems for data encryption and backup. The more sophisticated their tools, the better your defense.
· Customer Service: Here's where many fall short. Your CSaaS provider should be your trusty sidekick, ready 24/7 to support you through any cyber onslaught or query you might have.
· Scalability: Your business will grow, and so should your cybersecurity measures. Whether you're a quaint café or a sprawling enterprise, your CSaaS solution should scale seamlessly alongside you, offering cybersecurity as a service for small businesses and large ones alike.
While these metrics are needed, the first thing you’d need to do is show what your business needs help with. Only when you’re set on that can you seek help from top-notch cybersecurity service providers.
How Do Businesses Implement CSaaS?
Implementing CSaaS isn’t about flipping a switch; it takes dedication, time, and effort from all sides. You need the right conditions, a bit of patience, and the know-how to see it thrive. Here’s your five-step green-thumb guide to CSaaS implementation:
1. Assessment: Start by taking stock of where you stand in the cyber world. What's your current cybersecurity posture? What are the specific threats to your industry? The answer to these questions will help tailor the CSaaS to your needs.
2. Integration Plan: Work closely with your chosen cyber security service provider to map out how their services will integrate with your existing systems. This might involve some digital transformation, but it’s all in the name of security.
3. Rollout: Begin with a phased approach. Test the waters with a few critical systems before going all in. Understand your security risk and security policies before fully implementing your security solution.
4. Training: Don't overlook this. Ensure your team knows the basics of cybersecurity awareness. After all, the most sophisticated security technologies can be undone by a simple human error.
5. Feedback Loop: Set up a clear channel of communication with your CSaaS provider. Regular check-ins will help you stay ahead of emerging threats and adapt your strategies as needed.
The Future of CSaaS
The future of Cybersecurity-as-a-Service (CSaaS) is shining brightly, fueled by advancements in AI and Machine Learning. These digital technologies are paving the way for a proactive, predictive approach to cybersecurity, allowing systems to predict cyberattacks before they occur. This proactive stance is rapidly becoming a reality.
Moreover, the adoption of Zero Trust Security principles, based on a "never trust, always verify" approach, is fortifying our digital defenses and significantly reducing the risk of insider threats.
Beyond individual or organizational efforts, the cybersecurity landscape is seeing a new era of Global Cybersecurity Collaboration, transcending borders to unite against common cyber threats such as phishing, malware, personal data breaches, and more.
This collective endeavor, combined with an increased focus on customization, ensures that CSaaS solutions are not only powerful but also uniquely tailored to meet the diverse needs of businesses across various industries.
How Pipeline Protects
At Pipeline, we understand the challenges businesses face nowadays with security threats and malicious actors being ever-present. That is why we stand as an unwavering force, providing robust cybersecurity defense.
With our deep-rooted ability, particularly in the dynamic Asian market, we offer an impenetrable wall against the multitude of cyber vulnerabilities and risks confronting businesses.
Our suite of cutting-edge security solutions and services is meticulously designed to address cyber threats from every angle. Our Advanced Log Analytics with DatalaiQ empowers organizations to harness their log data for enhanced monitoring and real-time analysis of potential breaches and security incidents.
Our Secure Internet Gateway, ThreatIDR, and Managed Endpoint Security, ThreatMDR, act as robust security controls, shielding digital assets from internet-based threats, endpoint cyber attacks, and unauthorized access.
Moreover, our research on the Dark Web provides actionable intelligence, enabling us to pre-empt attacks and stay ahead of security threats. As cyber threats evolve, we continuously evolve our strategies with them.
At Pipeline, we create an environment where your business can thrive securely and confidently, safeguarded by our unwavering commitment to cybersecurity excellence. We make sure your business never misses the feeling of having an in-house team.
If you're seeking a trusted partner to navigate the complexities of cybersecurity, contact us today. Our team of experts is ready to fortify your defenses, safeguard your digital assets, and empower your business with unparalleled cybersecurity solutions.









