Digital transformation is propelling businesses towards innovative horizons, and the shadow of cyber threats is looming larger by the day. Navigating this complex landscape requires a nuanced approach to cybersecurity, blending innovative technology with deep domain expertise. This is where cybersecurity consulting services become pivotal in elevating a company's security posture.
Thus, elevating your security posture with cybersecurity consulting services is essential for your establishment - since traditional cybersecurity services are not good enough. With the choppy waters of cybersecurity challenges, here’s how Pipeline, Inc. can have a transformative impact on a business’s resilience to cyber threats.
Let’s begin by learning how global cybersecurity consulting services protect your business and how you can contribute to it.
What is Security Posture?
A strong security posture refers to the overall security status of a software environment, information systems, or organization, encompassing the strength of its defenses against cyber threats and attacks.
Cybersecurity posture involves a comprehensive evaluation of your IT security measures, risk management strategies, and implementing security policies and protocols designed to protect against vulnerabilities, malware, and unauthorized access.
Enhancing your security posture means safeguarding data and network security and ensuring that security solutions, such as firewalls, encryption, and intrusion-detection systems, are effectively managed and updated to combat the latest cyber-security challenges.
Businesses aiming to bolster their security posture must prioritize regular security assessments, threat analysis, and employee security training to build a resilient defense against evolving security threats and cyber-attacks.
The Importance of Cybersecurity Consulting for Businesses
Cybersecurity is not just about implementing the latest security technologies; it's about crafting a strategic approach encompassing risk management, data protection, and threat analysis. Companies that excel in cybersecurity see their shareholder returns nearly four times compared to those with simpler security setups.
Cybersecurity consulting services offer a comprehensive overview of your current security posture, identifying vulnerabilities and recommending actionable steps towards improvement. This isn't about safeguarding data; it's about ensuring business continuity in the face of evolving cyber risks.
For businesses, engaging in cybersecurity consulting isn't just a precautionary measure; it's a strategic investment. Pipeline, Co., a global leader in cybersecurity solutions, emphasizes that cybersecurity consulting is foundational in developing a robust security infrastructure.
The Pillars of Cybersecurity Consulting Services
With services ranging from threat analysis to security assessments and risk management, consulting firms play a crucial role in shaping the security strategy that underpins a business's defense mechanisms against cyber threats. Let’s see the pillars of cybersecurity consulting below.
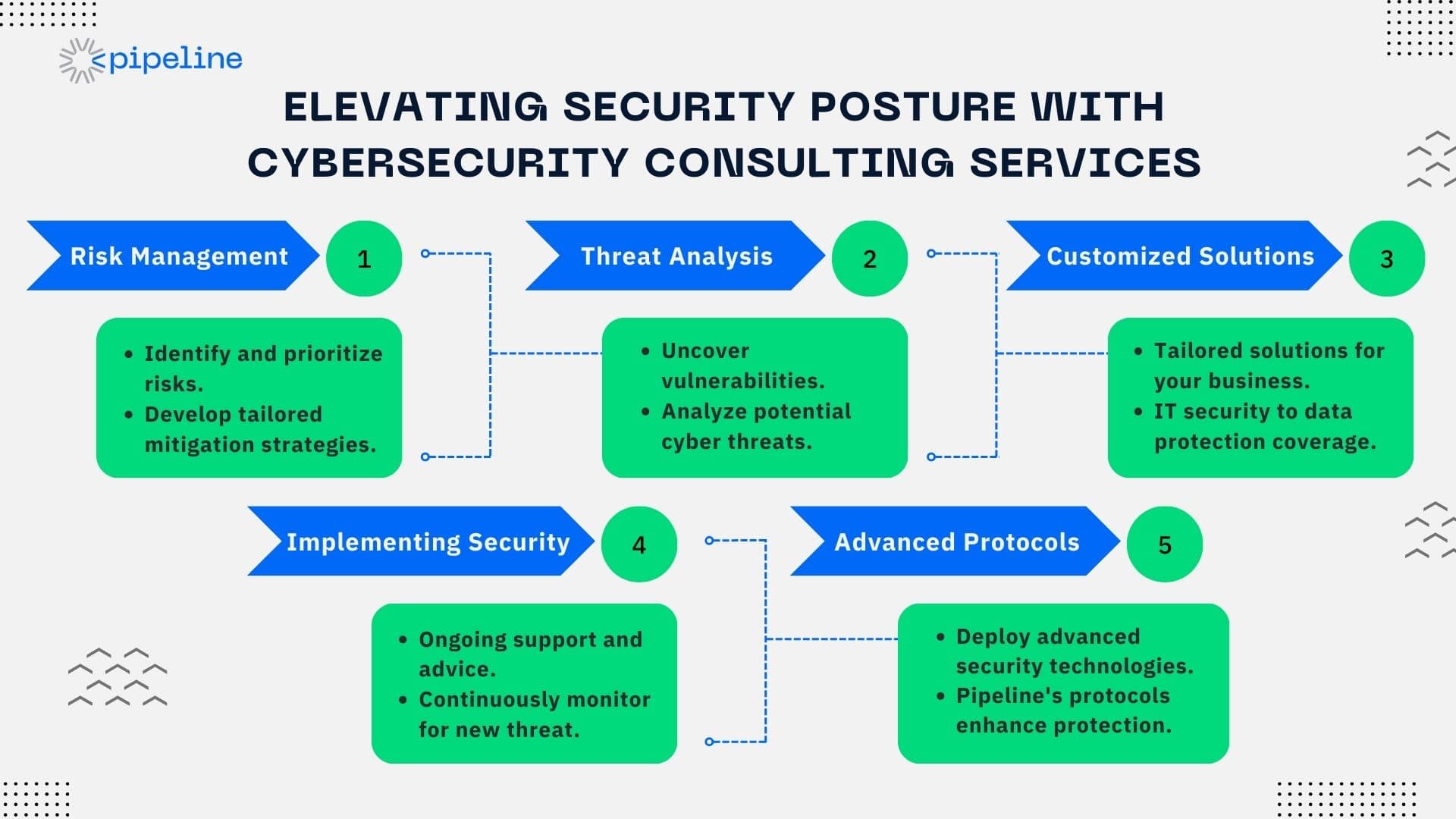
Cyber Risk Management
Cyber risk management is at the heart of cybersecurity consulting. It's a process that begins with understanding a business's specific threats and extends to developing a comprehensive strategy to mitigate those risks.
Cyber risk management involves evaluating the potential impact of cyber threats and implementing security measures tailored to the business's unique needs.
Security Assessment and Threat Analysis
A thorough security assessment is the first step in uncovering the gaps in a business's security framework. By evaluating existing security measures against best practices in network security and data protection, consultants can identify areas of improvement.
Threat analysis goes a step further by identifying potential threats and their impact on the business, enabling the development of a proactive defense strategy. Pipeline, Inc. strives for continuous automated red teaming (CART), which is also strongly required in threat analysis.
Tailoring Cybersecurity Solutions
When it comes to cybersecurity, one size does not fit all. Tailored cybersecurity solutions are essential for addressing each business's specific challenges and needs.
Whether enhancing IT security for a tech startup or implementing industry-specific security solutions for a financial services firm, customized advice and solutions are critical for effective cybersecurity.
Best Practices in Cybersecurity Consulting for Elevating Security Posture
When it comes to bolstering your cybersecurity defenses, the expertise and insights provided by cybersecurity consulting services can be invaluable. Drawing from a vast pool of experience and a comprehensive understanding of the cyber landscape, consultants offer tailored strategies that align with your business's needs.
Here's how we make a difference in elevating your establishment’s security posture:
- Comprehensive Security Assessment Services
Before you can fortify your defenses, you must know where your vulnerabilities lie. Cybersecurity consultants conduct thorough assessments that cover every aspect of your organization's security posture, from network security to data protection, offering a clear roadmap for improvement.
- Implementing Effective IT Security Measures
In the rapidly evolving cyber landscape, staying ahead of threats requires more than just a set-and-forget approach to security. Consultants recommend and help implement the latest IT security measures, ensuring your defenses remain robust against emerging threats.
- Tailored Cybersecurity Solutions for Small Businesses
Recognizing that small businesses have unique needs and constraints, cybersecurity consultants provide solutions that are effective, scalable, and budget-friendly.
- Evaluating Cybersecurity Threats with Expert Consultants
The dynamic nature of cyber threats means that what worked yesterday may not work today. Consultants continuously evaluate the threat environment, ensuring that your security strategies evolve as needed.
- Using AI and ML to Enhance Cybersecurity Posture
Using AI and ML for protection against various cyber security threats has become quintessential. When using AI and ML in cybersecurity, network traffic behavior can be monitored flawlessly, as performed by Pipeline, Inc.’s services.
The insights gained through these services empower businesses to make informed decisions, leading to enhanced security measures that protect against current and future cyber threats.
The Role of Cybersecurity Consultants in Risk Management
Risk management is a cornerstone of effective cybersecurity strategy; cybersecurity consultants are instrumental in its execution. Our expertise allows them to identify the threats businesses face today and those that could emerge tomorrow.
Our services jump right in to perform their roles in cybersecurity consultancy in risk management through:
- Identifying Vulnerabilities with Cybersecurity Risk Assessments
By thoroughly assessing a company's security infrastructure, consultants can pinpoint vulnerabilities that might be exploited by cybercriminals and guide the development of strategies to address these weaknesses.
- Cybersecurity Roadmap Planning and Implementation Services
Consultants identify risks and help businesses plan and implement a cybersecurity roadmap that addresses these risks in a structured, prioritized manner.
- Cybersecurity Advisory for Digital Transformation Projects
As businesses undergo digital transformation, consultants ensure that cybersecurity is an integral part of the process, thus safeguarding the future digital infrastructure of the company.
- Integrating Cybersecurity Best Practices into Business Operations
Consultants like Pipeline, Inc. provide guidance on incorporating cybersecurity best practices into daily business operations, enhancing overall resilience to cyber threats.
The role of cybersecurity consultants in risk management cannot be overstated. By identifying risks, planning mitigation strategies, and guiding the implementation of these strategies, consultants ensure that businesses are protected against current threats and prepared for future challenges.
Strengthening Security Infrastructure with Expert Consultations
A robust security infrastructure is the backbone of any effective cybersecurity strategy. Cybersecurity consultants are key players in strengthening this infrastructure, offering insights that span the latest technological advancements to regulatory compliance.
Our contribution to strengthening security infrastructure include:
- Understanding that each industry faces unique threats and regulatory requirements, consultants tailor security solutions to meet these specific needs.
- Proactive consulting helps organizations avoid cyber threats by implementing forward-thinking strategies and technologies before breaches occur.
- Navigating the complex landscape of cybersecurity regulations can be daunting. We provide expert advice on compliance, ensuring that businesses meet all cybersecurity-related legal and regulatory requirements.
- With the landscape of cyber threats constantly evolving, having advanced threat detection and response capabilities is crucial. Consultants help businesses implement these systems, significantly reducing the risk of a successful cyber-attack.
- Security Posture Management (SPM) is still a huge challenge for businesses; our expertise protects and elevates your security posture.
The strategic insights provided by cybersecurity consultants in strengthening security infrastructure are invaluable. By leveraging our expertise, businesses can ensure that their cybersecurity measures are reactive and proactive, offering robust protection against an ever-changing threat landscape.
Navigating through Cybersecurity Posture Vulnerabilities
Vulnerabilities stand as the Achilles' heel that attackers exploit to compromise the integrity of information systems. These weaknesses can range from software flaws to inadequate security policies, each serving as a potential entry point for malicious actors.
Cybersecurity consulting services play a crucial role in vulnerability management, identifying and prioritizing these vulnerabilities for remediation. This process involves penetration testing, vulnerability assessments, and robust security controls to safeguard against intrusion and ensure confidentiality, as seen below.
- Conducting Regular Vulnerability Assessments: Identifying potential weaknesses before attackers do is a critical defense strategy. Security experts recommend regular assessments to stay ahead.
- Implementing Strong Authentication and Access Control Measures: To prevent unauthorized access, it's essential to implement multifactor authentication and define strict access control policies.
- Adopting Comprehensive Security Solutions: From firewalls and encryption to intrusion detection systems, a layered security approach is key to defending against a wide range of threats.
Vulnerability management is not a one-time task but a continuous cycle of identifying, assessing, treating, and monitoring vulnerabilities to effectively enhance enterprise security and mitigate security risks.
Protection Against Malware and Ransomware Attacks
Malware and ransomware represent some of the most insidious threats in the cyber landscape, capable of compromising, encrypting, or even wiping critical data. Cybersecurity consultants emphasize the importance of proactive measures in protecting against these malicious threats.
Utilizing advanced threat detection tools, implementing endpoint protection, and conducting employee security training are foundational steps in building resilience against malware and ransomware.
Active protection against ransomware attacks can be achieved through:
- Educating Employees on Phishing and Social Engineering Tactics: Awareness training can significantly reduce the risk of employees inadvertently downloading malware or falling victim to phishing scams.
- Deploying Advanced Malware Protection Solutions: Security technologies that detect and neutralize malware in real time are critical components of a robust security framework.
- Ensuring Regular Data Backups and System Updates: Regular backups and updates can help mitigate the damage caused by ransomware attacks and ensure data integrity. Learn more about CSaaS through our comprehensive guide.
Malware and ransomware defense is a multifaceted endeavor that requires ongoing vigilance, state-of-the-art security technology, and a culture of cybersecurity awareness within the organization.
Securing Digital and Physical Frontiers: A Holistic Approach
In today's interconnected world, security is not just about safeguarding digital assets but also the physical security of hardware and premises. Cybersecurity consulting services advocate for a holistic security strategy integrating cybersecurity measures with physical security protocols.
This comprehensive approach ensures that all potential entry points are secured against adversaries, whether from hackers trying to breach your network or unauthorized personnel attempting to access your physical infrastructure.
- Integrating Physical Security with Cybersecurity Policies: Aligning security policies to cover digital and physical security aspects ensures a unified defense posture.
- Employing Forensic and Incident Response Capabilities: In the event of security breaches, having a team ready for digital forensics and incident response is crucial for swift remediation and minimizing impact.
- Leveraging Security Information and Event Management (SIEM): SIEM solutions provide real-time analysis and reporting of security alerts generated by applications and network hardware, bridging the gap between cyber and physical security.
Achieving a holistic security posture demands an integrated approach, leveraging cybersecurity and physical security measures to protect against the full spectrum of threats.
Cybersecurity in the Age of Cloud and Mobile Computing
As businesses increasingly adopt cloud-based services and mobile computing, the cybersecurity landscape evolves, presenting new challenges and opportunities. Cloud and mobile security have emerged as critical domains within cybersecurity consulting, focusing on securing data outside the traditional network perimeter.
This shift requires adapting security strategies to protect confidential information across cloud environments and mobile devices, ensuring data security and compliance with regulations like HIPAA.
- Implementing Cloud-Based Security Solutions: Utilizing cloud-based security services can provide scalable and flexible security solutions that match the dynamic nature of cloud computing.
- Enhancing Mobile Security Practices: Adopting comprehensive mobile security measures, including application security, device management, and secure communication protocols, is essential in safeguarding mobile data.
- Adapting Security Policies for Remote Work: As remote work becomes more common, updating security policies to address the risks associated with off-premises data access is crucial.
The move towards cloud and mobile computing requires a forward-thinking approach to cybersecurity that anticipates and mitigates the evolving threats in these rapidly expanding sectors.
Please check our blog on why you need CSaaS for businesses in this age.
Please check our blog on why you need CSaaS for businesses in this age.
By staying abreast of the latest developments in cloud security and mobile security, businesses can leverage the benefits of these technologies while minimizing their potential risks.
How Pipeline Protects
In the swiftly evolving digital realm, where cyber threats loom large and constant, understanding the role and capabilities of your cybersecurity partner is paramount. Pipeline stands at the forefront of cybersecurity innovation in Asia, offering a shield against daily digital dangers businesses face. Our commitment to cybersecurity is not just about providing solutions; it is about offering peace of mind.
Our suite of products, including DatalaiQ for advanced log analytics, Fense for innovative email security, ThreatIDR for secure internet access, and ThreatMDR for managed endpoint security, ensures comprehensive protection across all digital fronts. With the addition of Pipeline Security Intelligence Vision, we deliver actionable insights and intelligence on emerging threats, enabling businesses to stay one step ahead.
Our services extend from risk analysis consulting, designed to fortify your security posture, to incident response services for rapidly mitigating cyber incidents, and dark web research to pre-empt potential threats.
At Pipeline, we are not just responding to cybersecurity challenges but anticipating them, ensuring that your business is safeguarded with the most advanced and effective defenses available. Trust Pipeline to be your 24/7 guardian in the digital age, keeping your operations secure and your data protected.