With AI’s evolution in information-security’s arena, IoT security stands as a critical frontier against cyber threats. Thus, enhancing IoT security strategies in 2024 has become essential for enterprises and individuals.
With billions of connected devices interwoven into the fabric of daily life, the necessity for robust security measures has never been more pronounced. To ensure you and your business is protected in a 360-degree coverage in the world of IT security, you need strategies to master IoT security strategies, risks, and top solutions.
With our years of expertise in protecting individuals and businesses from cyber-attacks, we’re here to provide you with the most valuable information on security awareness. Let’s delve into the security strategies you can be taking to master your information-systems and stay on the safer end through IoT security.
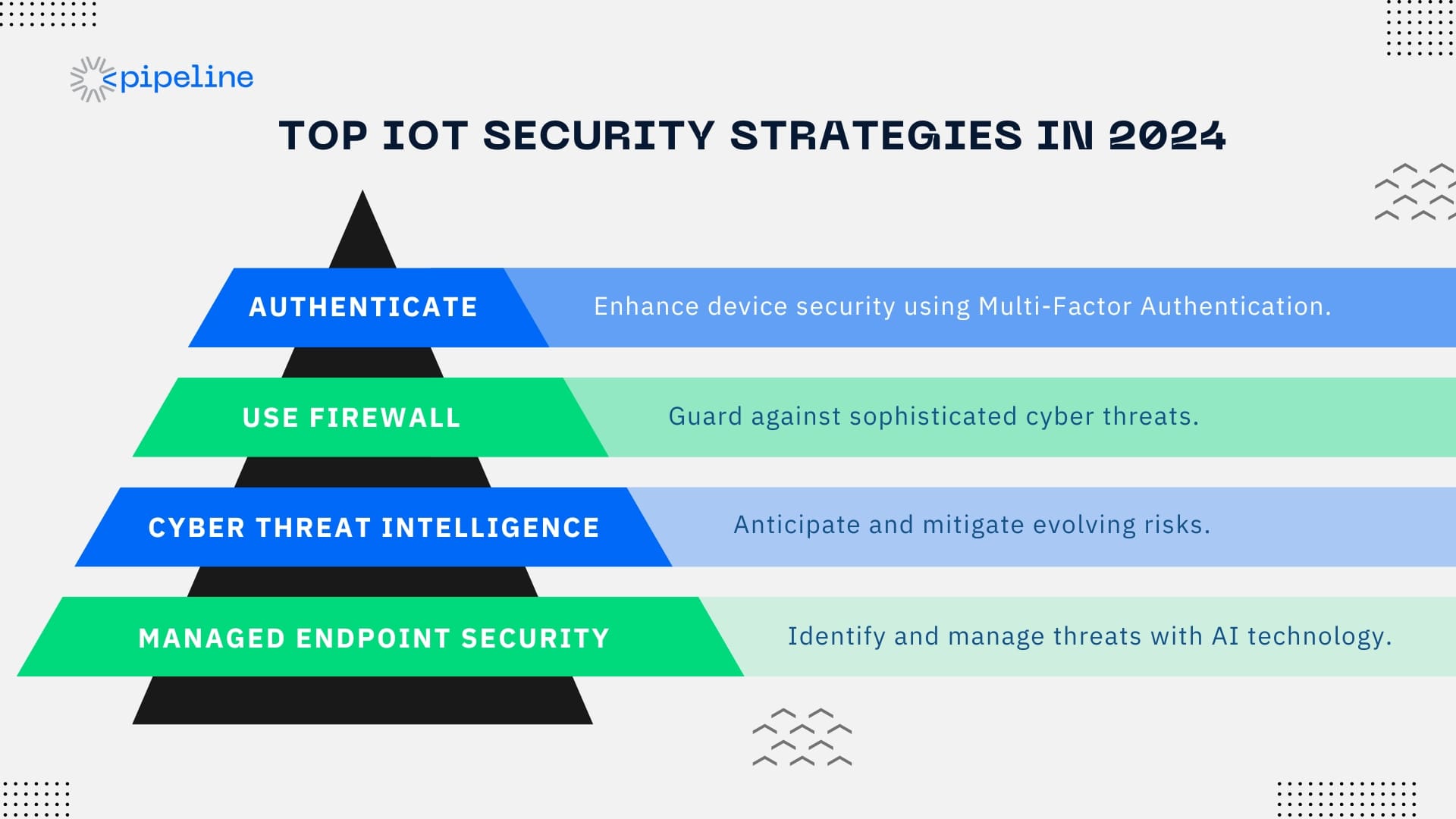
Best Practices for IoT Security in 2024
The foundation of IoT security lies in adherence to best practices that ensure the integrity and confidentiality of connected ecosystems. These practices are not just recommendations; they are essential pillars for safeguarding IoT devices.
Here’s what you can do to enhance your IoT security in 2024:
- Regular Firmware Updates: Keeping device firmware updated is crucial for closing security vulnerabilities.
- Secure Authentication Protocols: Implement robust authentication methods, including multi-factor authentication, to enhance device security.
- Network Segmentation: Dividing network components into secure zones can minimize the impact of potential breaches.
Firewall Innovations: The First Line of Defense
A startling revelation from cybersecurity news highlights that over 50% of cyber-attacks target small to medium-sized businesses, exploiting their often less fortified defenses.
Firewalls stand as the first line of defense, evolving to offer dynamic protection mechanisms that filter out malicious traffic and prevent unauthorized access to IoT devices. In today’s age, DNS firewall CAGR is projected for a 21.4% jump from 2023 to 2032. Implementing next-generation firewalls with integrated intrusion prevention systems can significantly enhance the security of sensitive data across the IoT ecosystem.
Implementing these practices is the first step toward a secure IoT environment, reducing the attack surface available to cybercriminals.
Strategies to Mitigate IoT Security Risks
Mitigating risks in IoT networks involves a proactive approach, focusing on both prevention and readiness to respond to security incidents.
Alongside taking the help fo CTI (Cyber Threat Intelligence) provided by cybersecurity professionals, you can have a security strategy:
- Comprehensive Risk Assessments: Regularly evaluate your IoT ecosystem for vulnerabilities.
- Data Encryption: Utilize strong encryption standards for data at rest and in transit to protect sensitive information.
- Incident Response Planning: Have a clear, actionable plan for responding to security breaches.
Vulnerability Management to Mitigate IoT Security Risks
A recent report by Statista unveiled that 72.7% of all organizations fell prey to a ransomware attack, showcasing the relentless evolution of malicious software. Combatting this menace requires IoT systems to integrate advanced cybersecurity solutions capable of real-time malware detection and eradication.
Leveraging machine learning algorithms to predict and neutralize threats before they infiltrate the network ensures the protection of personal and confidential information against sophisticated malware and ransomware attacks.
By adopting these strategies, organizations can significantly reduce their exposure to IoT security threats and enhance their resilience against attacks.
IoT Security Solutions for Small Businesses
Small businesses often face unique challenges in securing their IoT devices, primarily due to limited resources. However, there are targeted solutions that can offer robust security without overwhelming costs.
Here’s how small businesses (SMB’s) can leverage IoT security solutions to their benefit:
- Cloud-Based Security Services: Leverage cloud services for scalable, cost-effective security solutions.
- Managed Security Service Providers (MSSPs): Consider outsourcing security management to specialists who can provide comprehensive protection.
- Simplified Security Tools: Utilize user-friendly security platforms that do not require extensive technical expertise.
Access Control in Security and Compliance
Strengthening IoT ecosystems involves rigorous access management protocols, ensuring that only authenticated users and devices can access network resources.
Implementing stringent security controls, such as multi-factor authentication and role-based access control, significantly mitigates the risk of unauthorized access and potential security breaches.
For small businesses, these solutions offer a pathway to robust IoT security, balancing cost with the sophistication of defense mechanisms.
Elevating IoT Security in the Cybersecurity Ecosystem
Cybersecurity, especially within the IoT domain, is more critical than ever. Recent statistics indicate a surge in cybercrime, with IoT devices increasingly becoming prime targets for hackers. This section explores key strategies to fortify IoT security within the broader cybersecurity framework.
Security Policies: Crafting a Robust Framework
According to IBM, there is a 71% year-over-year increase in cyberattacks that used stolen or
compromised credentials. Developing a robust security policy that encompasses all aspects of IoT operations is essential.
This policy should detail the security standards, practices, and technologies that form the organization's defense mechanism against cyber threats. Regular updates and training on these policies ensure that all stakeholders are equipped to safeguard against evolving cyber threats.
The Critical Role of Cybersecurity Experts in Risk Management
With cybercrime predicted to cost the world $10.5 trillion annually by 2025, the role of cybersecurity experts in risk management is more crucial than ever. Cybersecurity professionals employ a blend of threat intelligence, penetration testing, and security audits to identify vulnerabilities within IoT infrastructures.
Pipeline, Inc.’s expertise in crafting dynamic security strategies enables organizations to anticipate and neutralize potential threats, ensuring enduring protection against cyber attacks and ensuring compliance with security standards.
Enhancing IoT Security with Predictive Manufacturing
In the manufacturing sector, predictive analytics can transform IoT security from a reactive to a proactive stance.
Predictive manufacturing can managed through enhanced cyber-security measures:
- Anomaly Detection Systems: Use AI-driven systems to detect unusual behavior that may indicate a security threat.
- Predictive Maintenance: Anticipate and rectify security vulnerabilities before attackers can exploit them.
- Supply Chain Visibility: Monitor the security posture of all components in the supply chain to prevent infiltration.
Predictive manufacturing not only enhances operational efficiency but also acts as a formidable barrier against cyber threats.
Secure Remote Access for IoT Devices
As remote work becomes the norm, securing remote access to IoT devices is paramount. Whether it’s enterprise security or web-application security, a secure remote access for IoT devices can be attained through:
- VPN Solutions: Deploy Virtual Private Networks (VPNs) to create secure communication channels.
- Zero Trust Architecture: Implement a Zero Trust model, where trust is never assumed and must always be verified.
- Secure Access Service Edge (SASE): Use SASE frameworks to combine network security functions with WAN capabilities, ensuring secure remote access. SASE frameworks are now trusted with IoT protection levels.
Secure remote access ensures that the flexibility of remote work does not become a vulnerability in IoT ecosystems.
IoT Security for Manufacturing Automation
The integration of IoT in manufacturing automation has revolutionized production processes but also introduced unique security challenges.
Manufacturing automation cybersecurity is can be well attained through IoT security:
- Segmented Network Architecture: A segregated network ensures that a breach in one area does not compromise the entire manufacturing operation.
- Real-time Monitoring and Alerts: Utilize IoT security platforms for continuous surveillance of manufacturing systems to detect and respond to threats promptly.
Ensuring the security of IoT in manufacturing automation not only safeguards critical infrastructure but also maintains operational integrity and efficiency.
IoT Security Solutions for Healthcare Devices
Healthcare devices represent a critical area within IoT, where security directly impacts patient safety and data privacy.
Here’s how healthcare can be protected through IoT security solutions:
- End-to-End Encryption: All patient data transmitted by IoT devices must be encrypted to protect against unauthorized access.
- Regular Security Audits: Conduct comprehensive assessments to identify and rectify potential vulnerabilities in healthcare IoT devices.
By prioritizing security in healthcare IoT devices, providers can protect patient information and ensure the continuous, safe operation of medical equipment.
Secure IoT Device Management Techniques
Effective management of IoT devices is crucial for maintaining security across a network of interconnected devices.
To be security-risk free to your maximum extent, it’s important to secure IoT device management through personal techniques:
- Device Authentication: Implement strong authentication mechanisms to verify the identity of devices connecting to the network.
- Policy Enforcement: Establish and enforce security policies that govern the operation and interaction of IoT devices within the network.
Secure management practices ensure that IoT devices operate within defined security parameters, reducing the risk of compromise.
Protecting Against IoT Cyber Attacks
As IoT devices become increasingly prevalent, they become attractive targets for cyberattacks. Protecting these devices requires a proactive and comprehensive approach.
- Anomaly Detection: Employ AI-based systems to detect unusual patterns of behavior that may indicate a security threat.
- Security by Design: Incorporate security features at the design phase of IoT devices to build in resilience from the outset.
Protection against IoT cyberattacks demands ongoing vigilance and the adoption of advanced security technologies to detect and mitigate threats.
IoT Security Compliance and Regulatory Overview
Navigating the complex landscape of IoT security requires a thorough understanding of compliance and regulatory requirements.
At Pipeline, Inc. we follow the certain parameters for IoT security compliance and regulations:
- GDPR for IoT: Ensure that IoT data handling complies with General Data Protection Regulation (GDPR for IoT) standards.
- NIST Guidelines: Follow the National Institute of Standards and Technology (NIST) guidelines for IoT security.
- Sector-Specific Regulations: Be aware of any industry-specific regulations, such as HIPAA in healthcare, that impact IoT device usage.
Compliance not only avoids legal penalties but also guides the implementation of robust security measures.
IoT Security and Data Encryption Methods
Securing the vast amounts of data generated and transmitted by IoT devices is paramount for maintaining privacy and integrity.
Security experts rely solely on the following data encryption methods to stay on the safer end:
- Advanced Encryption Standards (AES): Use AES for secure data encryption, ensuring that data remains confidential and tamper-proof.
- Blockchain Technology: Explore the use of blockchain for secure, decentralized data management and authentication in IoT networks.
Employing robust encryption methods and innovative technologies like blockchain enhances data security within IoT ecosystems, ensuring that sensitive information is protected against unauthorized access.
How Pipeline Protects
In the ever-evolving landscape of digital threats, where cybersecurity risks loom larger than ever, the question arises: how can businesses navigate these turbulent waters to ensure their operations remain unscathed? This is where Pipeline steps in as your steadfast guardian in the digital realm.
Expertise in Cybersecurity, Tailored for Asia
Pipeline's deep understanding of cybersecurity nuances in Asia positions us uniquely to address and neutralize threats specific to this dynamic region.
Our team, available around the clock, is not just a group of experts; they are vigilant sentinels poised to respond to any cyber incident.
We specialize in transforming cybersecurity challenges into opportunities for strengthening your digital defenses, ensuring your business's integrity and continuity.
Innovative Products Designed for Comprehensive Protection
- DatalaiQ: Our advanced log analytics tool, DatalaiQ, empowers organizations with the capability to monitor, search, analyze, and visualize log data in real-time. This not only enhances visibility across your digital ecosystem but also enables proactive identification and mitigation of potential threats.
- Fense: With phishing attacks becoming increasingly sophisticated, our email security solution, Fense, acts as a robust shield, protecting your inbox and sensitive data from fraudulent emails and potential breaches.
- ThreatIDR: Our Secure Internet Gateway, ThreatIDR, provides immediate, robust protection against online threats, ensuring secure internet access across your organization.
- ThreatMDR: Managed Endpoint Security, or ThreatMDR, offers continuous, expert-driven detection and response, safeguarding your network from sophisticated threats through proactive monitoring and swift incident resolution. This is complemented by our Managed Cloud Security for Office365, ensuring a fortified cloud environment.
- Vision: Pipeline Security Intelligence, Vision, delivers real-time threat intelligence, equipping your organization with the insights needed to proactively defend against and adapt to the evolving cybersecurity landscape.
Customized Services for Unmatched Security
- Risk Analysis Consulting: Our security asessment alongside VAPT services delve deep into your cyber defenses to identify vulnerabilities, bolster your security posture, and equip both technical and executive teams with critical insights.
- Incident Response Services: In the event of a cyber incident, our rapid and comprehensive cyber security solutions ensure minimal impact, providing expert analysis, containment, and recovery strategies to swiftly restore security and confidence.
- Dark Web Research: Exploring the underbelly of the internet, our dark web research services offer valuable insights into potential threats and compromised data, preventing future cyber attacks using our Threat Intelligence and Operational Intelligence services.
In conclusion, Pipeline stands as a beacon of resilience in the face of cyber adversity. Through our bespoke products and services, we not only aim to protect but also to empower businesses with the knowledge, tools, and strategies required to navigate the digital age securely.

Trust Pipeline to be your ally in cybersecurity, safeguarding your digital journey every step of the way.