How cyber security analysts can make use of predictive analytics and stay ahead of just mere threat detection – prevention is the mitigation!
Imagine a world where cyber threats are identified and prevented before they even have a chance to cause havoc. Thanks to advanced data analytics, this futuristic scenario is becoming more of a reality.
Data analysis plays a crucial role in the fight against cyber threats. By analyzing vast amounts of data, analysts can uncover patterns and anomalies that indicate potential security breaches. This process, known as threat detection, allows organizations to stay one step ahead of cyber criminals.
But it doesn't stop there. With the help of cyber threat intelligence, data analysts can gather information about emerging threats and vulnerabilities. This knowledge enables proactive measures to be taken, preventing attacks before they occur.
One powerful use case in the arsenal of data analytics is anomaly detection. By identifying deviations from normal behavior within network traffic or user activity, analysts can quickly pinpoint potential threats and take immediate action.
But what if we could go beyond mere detection?
Enter predictive analytics. By leveraging historical data and sophisticated algorithms, organizations can forecast future cyber threats with remarkable accuracy. This proactive approach allows for preemptive security measures to be implemented, mitigating risks before they materialize.
From threat detection to anomaly detection and predictive analytics, these tools empower organizations to stay one step ahead in the ever-evolving landscape of cybersecurity. DatalaiQ by Pipeline is one of the data-analytics tools to mitigate the cyber threats.
In this blog, we’ll dive into the advanced data analytics with DatalaiQ by Pipeline, to mitigate the potential threats within the organization or infrastructure. So, rest easy knowing that behind the scenes, data analysts are working tirelessly to keep our digital world safe from harm.
How DatalaiQ Can Enhance Threat Detection and Response Efforts
If you're looking to level up your threat detection and response efforts, DatalaiQ this log analytics and correlation platform is here to lend a helping hand. With its impressive features and capabilities, this tool takes log analysis, network traffic analysis, and behavior profiling to the next level.
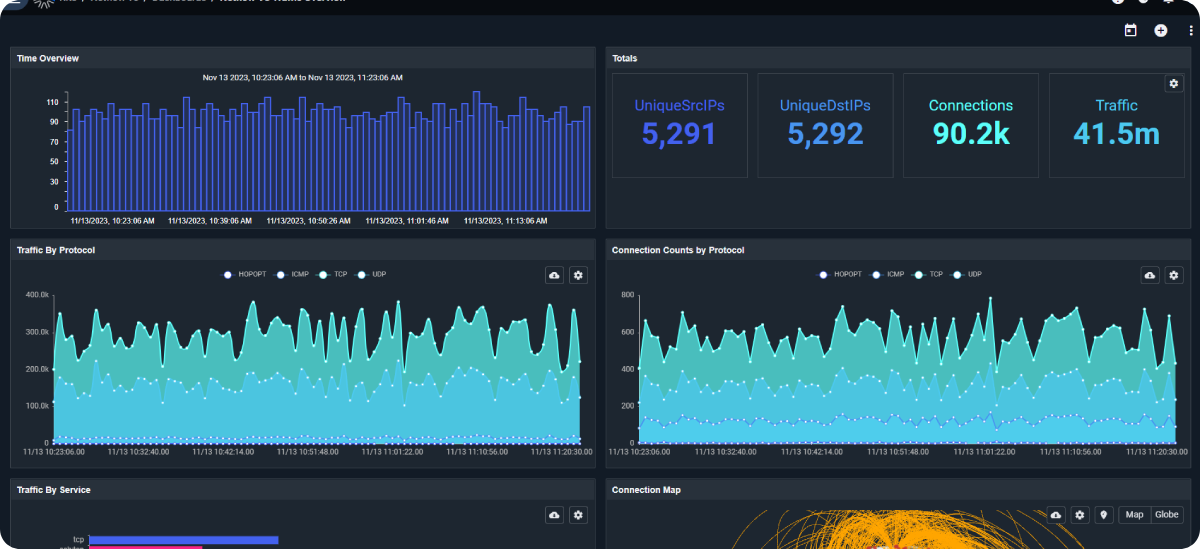
DatalaiQ's log analysis feature allows you to dig deep into your system logs, uncovering hidden patterns and anomalies that could be indicators of potential threats. By analyzing these logs in real-time, you can stay one step ahead of malicious actors and swiftly respond to any security incidents.
But it doesn't stop there - DatalaiQ the platform also excels in network traffic analysis. By monitoring and analyzing the flow of data within your network, it can detects suspicious activities or unauthorized access attempts. This enables you to proactively identify and address potential vulnerabilities before they turn into full-blown security breaches.
One of the standout features of the platform DatalaiQ is its behavior profiling capability. By creating profiles based on normal user behavior, it can quickly flag any deviations or unusual actions that may indicate a security threat. This helps you prioritize your response efforts and focus on the most critical issues at hand.
In a world where cyber threats are constantly evolving, having a tool like DatalaiQ a data analytics platform, capable of analysing any machine logs with security analytics capability, in your arsenal is invaluable. It not only enhances your threat detection capabilities but also empowers you to respond swiftly and effectively when faced with potential security incidents.
So why settle for anything less, when you can have DatalaiQ by your side?
Capturing and Analyzing Data for Effective Threat Mitigation with DatalaiQ
When it comes to effective threat mitigation, capturing and analyzing data is crucial. That's where DatalaiQ comes into play. With its powerful capabilities, DatalaiQ allows for seamless integration of various data sources, ensuring comprehensive coverage.
DatalaiQ It allows the central collection, management, and analysis of multiple types of log data generated by the system. Log data generated by firewalls, networks, and endpoints can be imported into DatalaiQ and used for correlational analysis,. This solution is ideal for system environments where multiple security solutions are in place mixed and management is complicated.complex and critical.
Being able to quickly import/ingest data from across the network and managing it centrally, is the job all security analyst dread and dreams of a solution to have in place.
DatalaiQ allows to quickly and centrally manage large amounts of log data. Log data from network devices and servers located at different points are imported in a cross-cutting manner.
The logs data can then be analyzed and visualized to detect suspicious illegal activities, investigate after security incidents, identify causes of system failures, improve performance, and more.
DatalaiQ apart from being used in enterprise-scale systems, but also for e-commerce sites and online games portals with users all over the world. The solution product is being introduced because of the following four great advantages:
· Rate plans based on data volume
· Flexible scalability
· Support for both text and binary data
· Expansion kits provide a wealth of functions
One of the key aspects of data collection is the methods used. DatalaiQ offers a range of flexible and efficient data collection methods, enabling organizations to gather information from diverse sources. Whether it's network traffic, system logs, or even sensor data, DatalaiQ can handle it all. What sets this solution apart is its ability to integrate these different data sources seamlessly. By bringing together information from multiple streams, organizations can gain a holistic view of its business and operations, and also potential threats and vulnerabilities. There are Kits, system built-in and custom, to analyze any type of data, as per user’s need.
With a robust platform and intuitive interface, capturing and analyzing data becomes a breeze for data and security analysts likewise. It empowers security teams to identify patterns, detect anomalies, and take proactive measures to mitigate threats effectively. So, if you're looking for a solution that simplifies the process of capturing and analyzing data for threat mitigation purposes, look no further than DatalaiQ. Its versatile capabilities and seamless integration with various data sources make it an invaluable tool in today's cybersecurity landscape.
Unleashing the Potential: Key Features and Capabilities of DatalaiQ
One of the key features of DatalaiQ is its ability to ingest and process data in real-time. This means, as soon as data is generated, DatalaiQ can capture it and analyze it instantaneously; no more waiting around for batch processing or delayed insights - you get up-to-the-minute information for proactive threat detection. It also goes beyond just ingesting data - provides advanced processing capabilities. It can handle large volumes of data from various sources, making it ideal for organizations dealing with petabytes of information. Whether it's network logs, system events, or security alerts, DatalaiQ can handle it all with ease.
The efficiency of threat detection is further enhanced by DatalaiQ's intelligent analytics engine. It uses machine learning algorithms and advanced analytics techniques to identify patterns, anomalies, and potential threats in real-time data streams. This allows security teams to stay one step ahead and respond quickly to emerging threats.
In summary, if you're looking to effortlessly handle real-time data ingestion and processing for efficient threat detection, it is recommended you book a call and have a demo. Its key features and capabilities will empower your organization to proactively safeguard against potential risks in today's fast-paced digital landscape.
Use Cases: How DatalaiQ Maximizes Threat Mitigation Efforts
Network security: Identifying suspicious network behavior and potential breaches
DatalaiQ is a powerful tool that goes beyond traditional threat detection to maximize threat mitigation efforts. With its advanced capabilities, DatalaiQ helps organizations identify suspicious network behavior and potential breaches, including the ever-present insider threats.
Insider threats: Detecting unusual employee activities and unauthorized access attempts
When it comes to insider threats, DatalaiQ excels at detecting any unauthorized or suspicious activities carried out by employees or trusted individuals within an organization.
It can track user behavior and flag any unusual actions that may indicate malicious intent or unauthorized access attempts.
Malware analysis: Analyzing patterns to identify new malware strains quickly
Furthermore, DatalaiQ's advanced analytics and machine learning capabilities allow it to correlate different data points and uncover hidden connections between seemingly unrelated events. This helps security teams gain a comprehensive understanding of the overall threat landscape and enables them to take proactive measures to mitigate risks effectively.
In summary, DatalaiQ plays a crucial role in maximizing threat mitigation efforts by identifying suspicious network behavior and potential breaches, including the ever-present insider threats. Its real-time analysis capabilities and advanced analytics empower organizations with the tools they need to stay one step ahead of cybercriminals and protect their valuable assets.
The Benefits of Implementing DatalaiQ in Threat Mitigation Strategies
Improved threat intelligence through comprehensive data analysis
If you're looking to level up your threat mitigation strategies, implementing DatalaiQ could be a game-changer. This powerful tool offers a range of benefits that can significantly enhance your security efforts.
One major advantage is improved threat intelligence through comprehensive data analysis. DatalaiQ enables you to gather and analyze data from various sources, allowing you to gain deeper insights into potential threats. By understanding the full scope of the risks, you can better prioritize and allocate resources for effective mitigation.
Reduced response time to mitigate threats effectively
Another key benefit is reduced response time. With DatalaiQ's advanced capabilities, you can quickly identify and assess threats, enabling faster decision-making and response.
This agility can make all the difference in preventing or minimizing the impact of an attack.
Enhanced scalability to handle large volumes of diverse data sources
Scalability is also a major advantage of implementing DatalaiQ. As the volume and diversity of data sources continue to grow, this tool can handle large amounts of information without compromising performance. Whether it's logs, network traffic, or other data types, DatalaiQ has got you covered.
By leveraging DatalaiQ in your threat mitigation strategies, you'll be equipped with comprehensive threat intelligence analysis, faster response times, and enhanced scalability - all crucial elements in staying one step ahead of potential security breaches.









