In this article, I will investigate the HDFC Bank Smishing Campaign that is currently widespread in India and abuses Web.app.
The aim of this article is to provide insight into current Smishing Campaigns.
In Smishing Text and Link Analysis, I will investigate the Smishing Text sample and where the link leads to.
In Reputation Checks and Domain Analysis, I will conduct Reputation Checks and Domain Analysis using VirusTotal, urlscan.io, and WHOIS.
In Sandbox Investigation, I will use a Sandbox to investigate the Phishing site’s behavior and view the contents and source code.
In OSINT Investigation, I will investigate the Smishing Campaign trends on Social Media, how threat actors used fake Twitter accounts to further their attacks, and how the official HDFC accounts responded.
In Threat Intelligence, I will look at the Threat Intelligence of Web.app, used in this phishing campaign.
In A Few Days Later…, I will check the status of the reputation checkers and phishing sites after some time has passed. I will also check the status of the fake Twitter accounts.
In Saving the Evidence, I will cover the usage of the Internet Archive and how it can be used to preserve digital evidence.
I did most of the investigation between March 4~5, 2023, so the information is subject to change.
Now let’s dive into the investigation of the deceptive HDFC Bank Text Scams!
The aim of this article is to provide insight into current Smishing Campaigns.
In Smishing Text and Link Analysis, I will investigate the Smishing Text sample and where the link leads to.
In Reputation Checks and Domain Analysis, I will conduct Reputation Checks and Domain Analysis using VirusTotal, urlscan.io, and WHOIS.
In Sandbox Investigation, I will use a Sandbox to investigate the Phishing site’s behavior and view the contents and source code.
In OSINT Investigation, I will investigate the Smishing Campaign trends on Social Media, how threat actors used fake Twitter accounts to further their attacks, and how the official HDFC accounts responded.
In Threat Intelligence, I will look at the Threat Intelligence of Web.app, used in this phishing campaign.
In A Few Days Later…, I will check the status of the reputation checkers and phishing sites after some time has passed. I will also check the status of the fake Twitter accounts.
In Saving the Evidence, I will cover the usage of the Internet Archive and how it can be used to preserve digital evidence.
I did most of the investigation between March 4~5, 2023, so the information is subject to change.
Now let’s dive into the investigation of the deceptive HDFC Bank Text Scams!
Smishing Text and Link Analysis
The text message looks like the following,
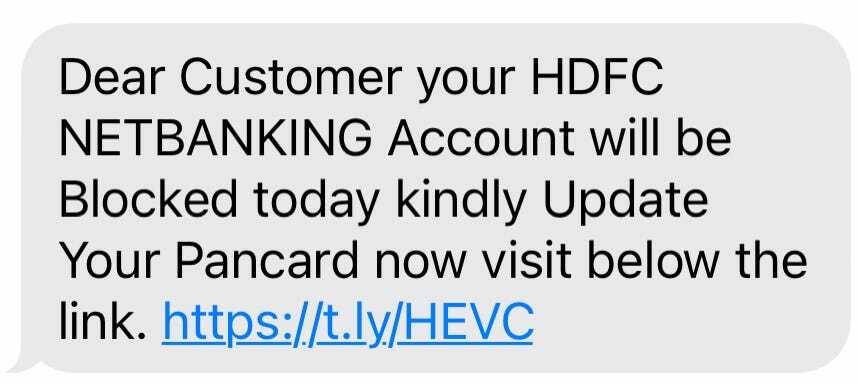
Dear Customer your HDFC NETBANKING Account will be Blocked today kindly Update Your Pancard now visit below the link. https://t[.]ly/HEVC
It contains the link https://t[.]ly/HEVC, a shortened link using t.ly. I went to the Redirect Checker to check for the original link and the redirects. I selected “BROWSER — Chrome 34” for the User-Agent.
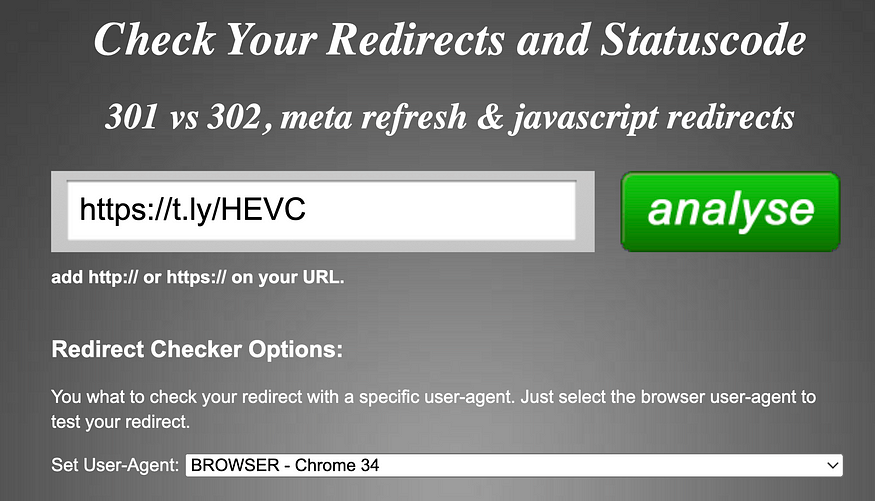
https://t[.]ly/HEVC has a status code of 301, and it redirects to https://hmj2utnme[.]web.app, which has a status code of 200.
The HTTP headers from Redirect Checker looks like the following,
>>> https://t.ly/HEVC
> --------------------------------------------
> 301 Moved Permanently
> --------------------------------------------
Status: 301 Moved Permanently
Code: 301
Date: Sat, 04 Mar 2023 13:54:06 GMT
Content-Type: text/html; charset=UTF-8
Connection: close
Location: https://hmj2utnme.web.app
set-cookie: tly_session=eyJpdiI6InZHdS9QMWNoUFlDUjZNblR0UWhUcnc9PSIsInZhbHVlIjoiTGprZ2MzWTdUQ1ZzOGxtTy9SUTNUVk1PRnZCMjFnNlIxckZUc3MxcGdidUNzZXY3RG5zRk4zR3VFSHFOZUJtNnZ6STRDVnJMYVk0RmZnQnU2M2p0YktzTmRRWUd0RnM5YTZQR3VDYnJFOEFlR1JmSlZSTlNqZVFGQXN5ZVlMT00iLCJtYWMiOiJhZjUzNmIwNjY1MDM0ZjlhZGIwODhkOTkwMWE1Y2IxZWIwZGIzZWQ3YjZlZGE3N2M2M2E1ZjdiOGQwMmNkYjZkIiwidGFnIjoiIn0%3D; expires=Sat, 18-Mar-2023 13:54:06 GMT; Max-Age=1209600; path=/; secure; httponly; samesite=lax
x-frame-options: SAMEORIGIN
x-xss-protection: 1; mode=block
x-content-type-options: nosniff
x-whom: tly-2
CF-Cache-Status: DYNAMIC
Report-To: {"endpoints":[{"url":"https:\/\/a.nel.cloudflare.com\/report\/v3?s=AropzU5bH5rzMoofA2w1l%2FMqh9TqYS5Jgbrhc5d4qxi2k73t%2FrY6DXBi2lZqc3i0%2Bp4Y0qTKFxPsoGGTBl3i5t1FAqTTxH3%2F6j1L1r93N9HM8d3EGes%3D"}],"group":"cf-nel","max_age":604800}
NEL: {"success_fraction":0,"report_to":"cf-nel","max_age":604800}
Strict-Transport-Security: max-age=15552000; includeSubDomains; preload
Server: cloudflare
CF-RAY: 7a2a9bf41f78383b-FRA
alt-svc: h3=":443"; ma=86400, h3-29=":443"; ma=86400
>>> https://hmj2utnme.web.app
> --------------------------------------------
> 200 OK
> --------------------------------------------
Status: 200 OK
Code: 200
Connection: close
Content-Length: 2281
Cache-Control: max-age=3600
Content-Type: text/html; charset=utf-8
Etag: "745b0de578e5968088d1c2de7154b4bbc78c819268297eb03d2c689d7d60e79e"
Last-Modified: Fri, 03 Mar 2023 08:38:09 GMT
Strict-Transport-Security: max-age=31556926; includeSubDomains; preload
Accept-Ranges: bytes
Date: Sat, 04 Mar 2023 13:54:06 GMT
X-Served-By: cache-hhn-etou8220064-HHN
X-Cache: HIT
X-Cache-Hits: 1
X-Timer: S1677938046.290518,VS0,VE1
Vary: x-fh-requested-host, accept-encoding
alt-svc: h3=":443";ma=86400,h3-29=":443";ma=86400,h3-27=":443";ma=86400Reputation Checks and Domain Analysis
In this section, I will be conducting reputation checks and domain analysis using urlscan.io, VirusTotal, and WHOIS information.
urlscan.io
I went to urlscan.io to analyze hmj2utnme[.]web.app, however, was not flagged as malicious at the time of investigation (March 4, 2023).
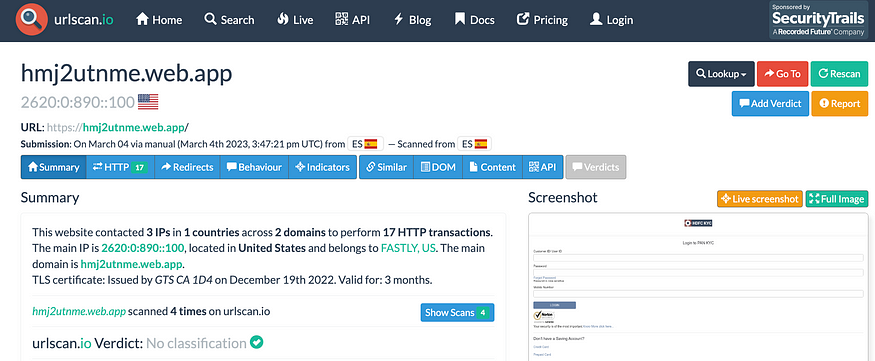
Although it was not flagged as malicious, there was other useful information. For example, it was seen contacting a few IPs.
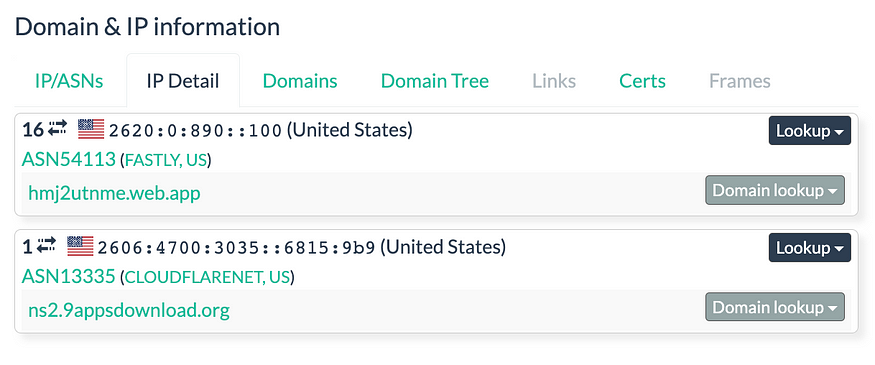
The full analysis on urlscan.io can be found below,
https://urlscan.io/result/1ae039a2-3441-4069-8b1e-374746a198a8/#summary
VirusTotal
I went to VirusTotal to analyze hmj2utnme[.]web.app, however only one(1) vendor has flagged it as phishing at the time of the investigation (March 4, 2023).
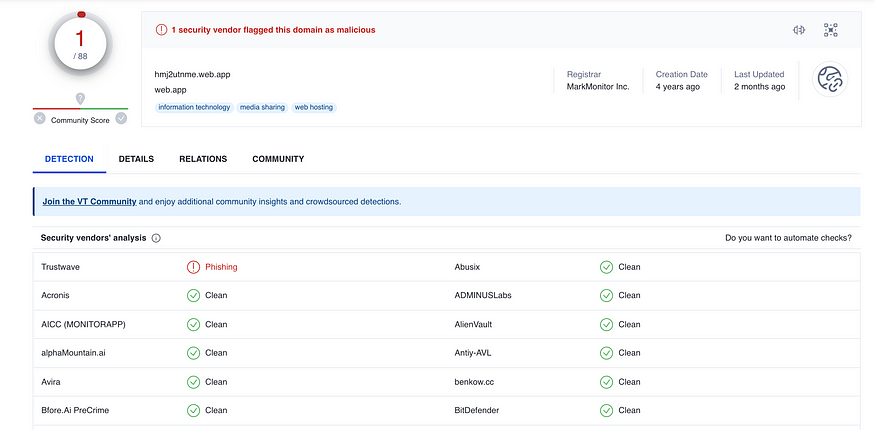
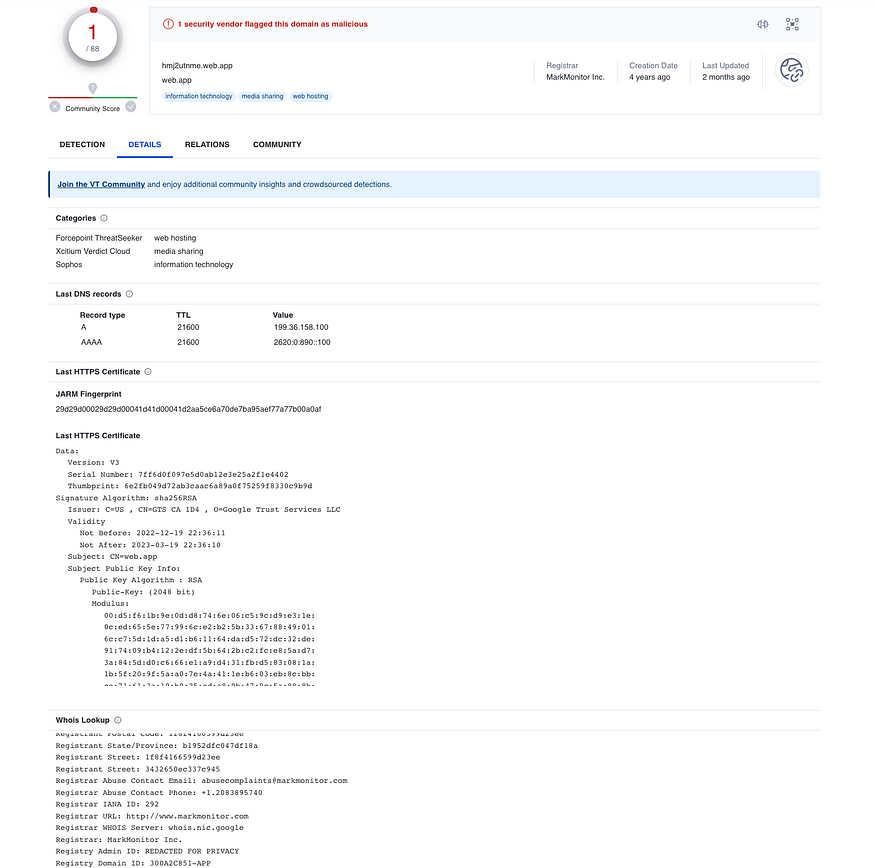
Although it was not flagged as malicious, there was other useful information here as well. For example, the HTTPS details, and the WHOIS information.
The full analysis on VirusTotal can be found below,
https://www.virustotal.com/gui/domain/hmj2utnme.web.app/detection
WHOIS
The WHOIS information looks like the following,
Admin City: REDACTED FOR PRIVACY
Admin Country: REDACTED FOR PRIVACY
Admin Organization: REDACTED FOR PRIVACY
Admin Postal Code: REDACTED FOR PRIVACY
Admin State/Province: REDACTED FOR PRIVACY
Creation Date: 2019-01-08T22:05:04Z
DNSSEC: unsigned
Domain Name: web.app
...
Registrar Abuse Contact Email: abusecomplaints@markmonitor.com
Registrar Abuse Contact Phone: +1.2083895740
Registrar IANA ID: 292
Registrar URL: http://www.markmonitor.com
Registrar WHOIS Server: whois.nic.google
Registrar: MarkMonitor Inc.
Registry Admin ID: REDACTED FOR PRIVACY
Registry Domain ID: 300A2C851-APP
Registry Expiry Date: 2024-01-08T22:05:04Z
...
Updated Date: 2022-12-12T09:28:46ZWe can see that the domain is Web.app, and is created in 2019. This is not flagged as malicious but has a poor community reputation.
These are some of the comments left by the community.
I will investigate the Web.app domain in the later section, Threat Intelligence.
Sandbox Investigation
In this section, I will be using a sandbox to investigate the behavior of the Phishing page.
Phishing Site’s Behavior
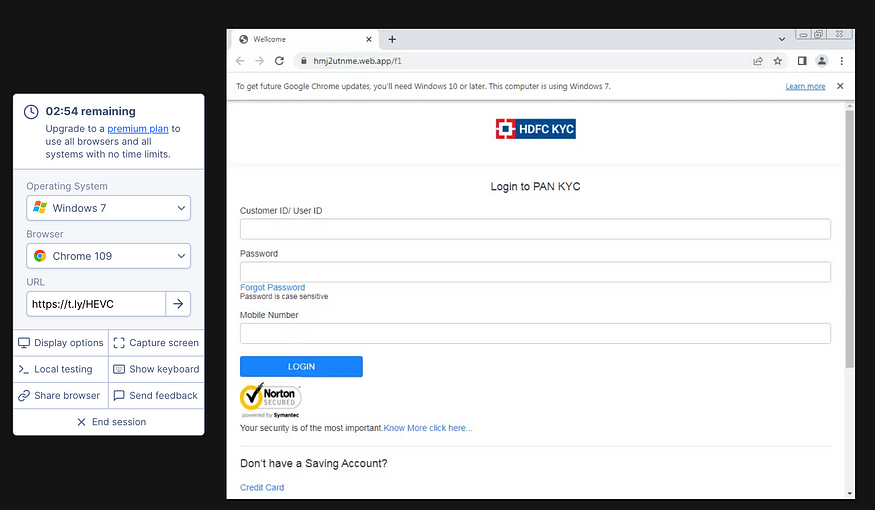
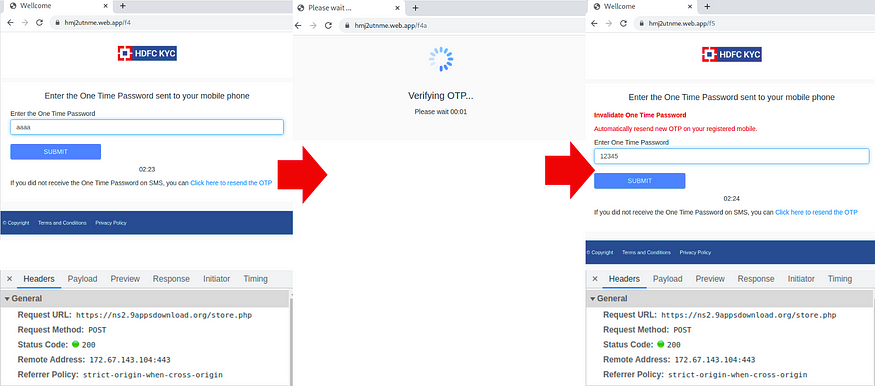
I went to Browserling to test the site’s behavior. Opening https://t[.]ly/HEVC leads to hmj2utnme[.]web.app/f1. It opened up a login page that impersonates HDFC Bank’s site.
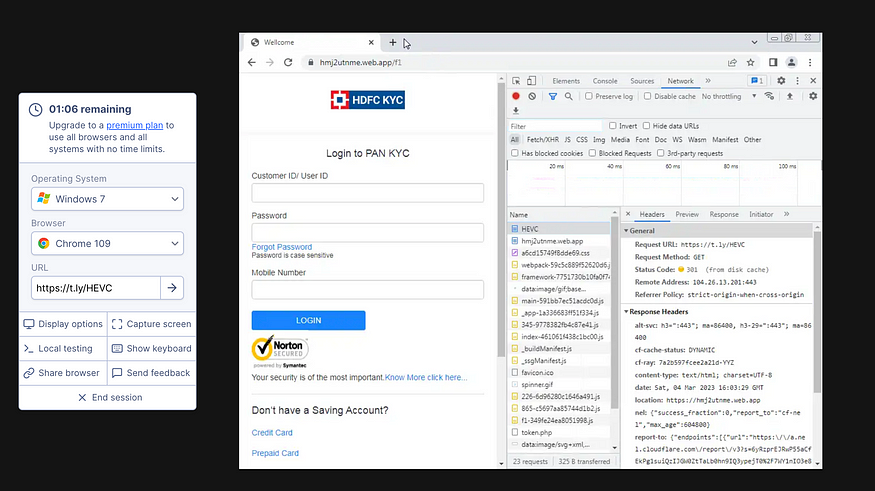
Viewing the HTTP Headers reveals that https://t[.]ly/HEVC had a status code of 301 as expected from the Redirect Checker.
It asked for User ID, Password, and Mobile Number. So I inputted random credentials.
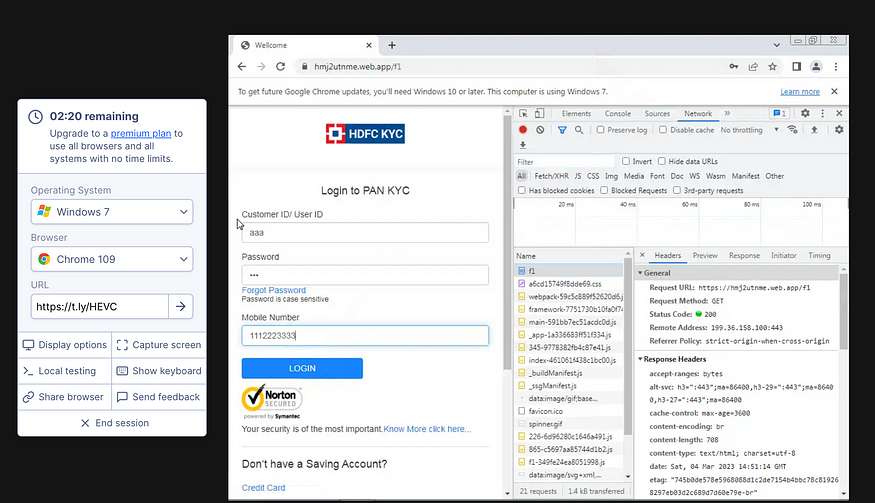
After clicking “LOGIN”, a POST to https://ns2.9appsdownload[.]org/store.php with the remote address 172.67.143[.]104 was seen.
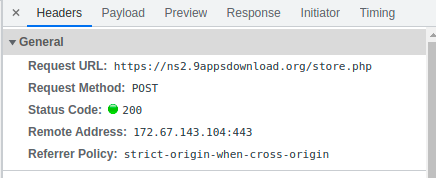
It then lead to hmj2utnme[.]web.app/f2, which then asked for the Account Holder Name and Date of Birth.
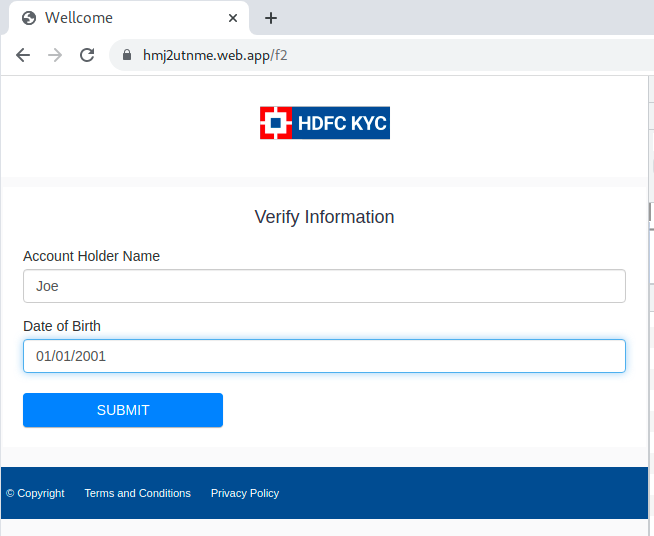
After clicking “SUBMIT”, a POST to https://ns2.9appsdownload[.]org/store.php with the remote address 172.67.143[.]104 was seen.
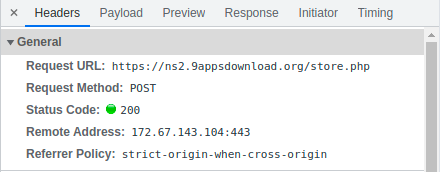
It then lead to hmj2utnme[.]web.app/f3, which showed “Verifying”, and a “Please Wait” countdown.
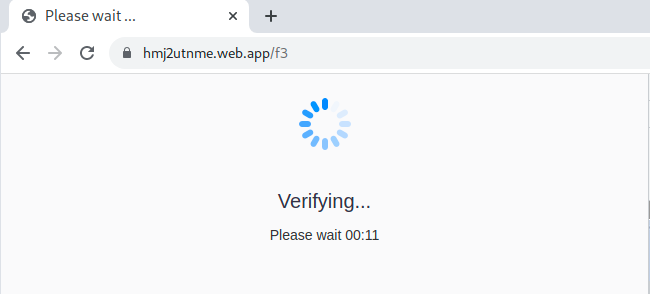
The entire behavior can be seen below, with the corresponding Headers upon clicking “SUBMIT”.
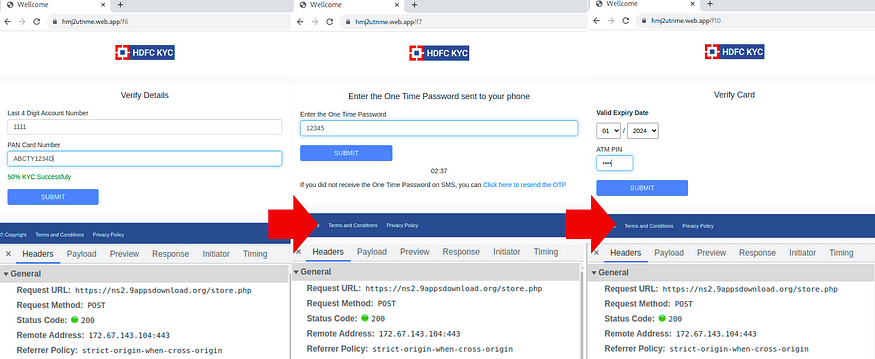
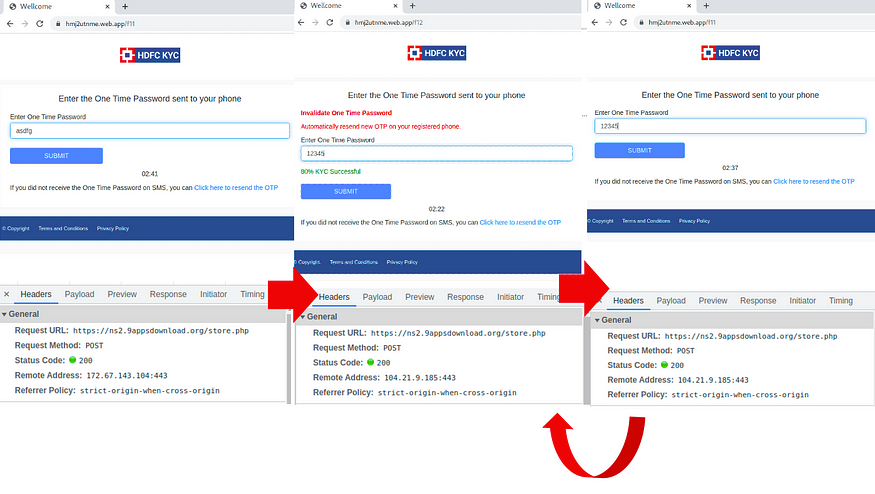
When inputting fake One Time Passwords, it loops between hmj2utnme[.]web.app/f11 and hmj2utnme[.]web.app/f12. The remote address for POST to https://ns2.9appsdownload[.]org/store.php becomes 104.21.9[.]185 after hmj2utnme[.]web.app/f12.
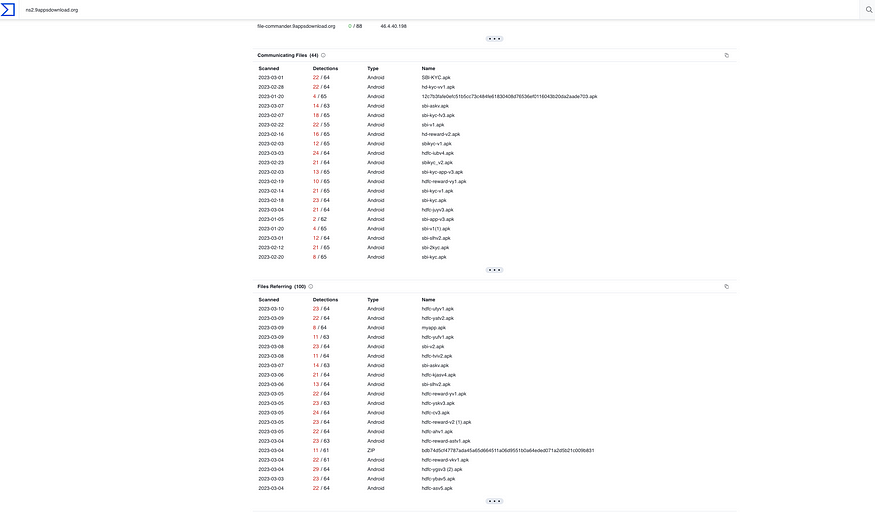
According to urlscan.io, there is a lot of Web.app and firebaseapp.com subdomains associated with ns2.9appsdownload[.]org.
According to urlscan.io, there is a lot of Web.app and firebaseapp.com subdomains associated with ns2.9appsdownload[.]org.
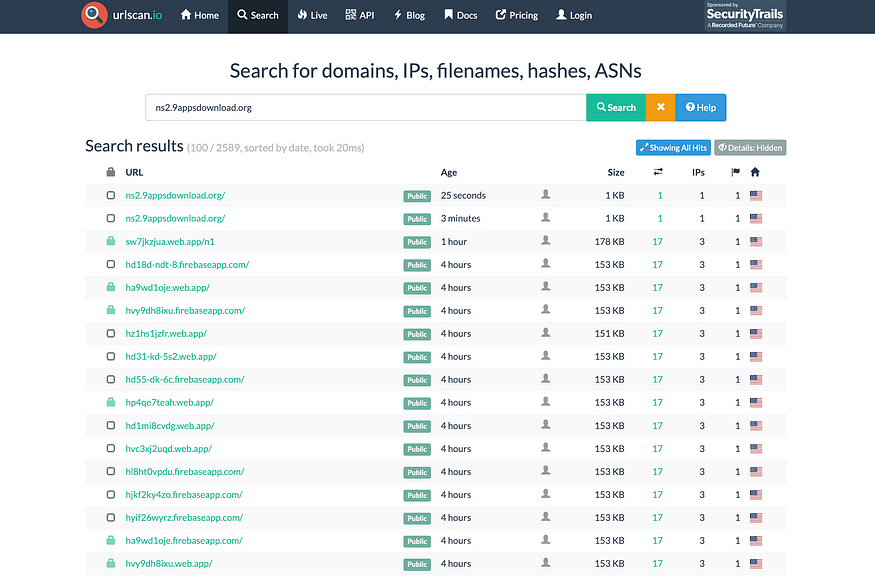
According to VirusTotal, there is a lot of malicious APKs associated with ns2.9appsdownload[.]org.
Phishing Site’s Source Code
The site’s source code was all in one line.
The source code looks like following:
<!DOCTYPE html><html><head><meta charSet="utf-8"/><meta name="viewport" content="width=device-width"/><title>Wellcome</title><meta name="next-head-count" content="3"/><link rel="preload" href="/_next/static/css/a6cd15749f8dde69.css" as="style"/><link rel="stylesheet" href="/_next/static/css/a6cd15749f8dde69.css" data-n-g=""/><noscript data-n-css=""></noscript><script defer="" nomodule="" src="/_next/static/chunks/polyfills-c67a75d1b6f99dc8.js"></script><script src="/_next/static/chunks/webpack-59c5c889f52620d6.js" defer=""></script><script src="/_next/static/chunks/framework-7751730b10fa0f74.js" defer=""></script><script src="/_next/static/chunks/main-591bb7ec51acdc0d.js" defer=""></script><script src="/_next/static/chunks/pages/_app-1a336683ff51f334.js" defer=""></script><script src="/_next/static/chunks/345-9778382fb4c87e41.js" defer=""></script><script src="/_next/static/chunks/pages/index-461061f438c1bc00.js" defer=""></script><script src="/_next/static/rYCyJCt1arYy2bGtPH3t1/_buildManifest.js" defer=""></script><script src="/_next/static/rYCyJCt1arYy2bGtPH3t1/_ssgManifest.js" defer=""></script></head><body><div id="__next"><div class="text-center loading-fast"><span style="box-sizing:border-box;display:inline-block;overflow:hidden;width:100px;height:100px;background:none;opacity:1;border:0;margin:0;padding:0;position:relative"><img alt="loading" src="data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7" decoding="async" data-nimg="fixed" style="position:absolute;top:0;left:0;bottom:0;right:0;box-sizing:border-box;padding:0;border:none;margin:auto;display:block;width:0;height:0;min-width:100%;max-width:100%;min-height:100%;max-height:100%"/><noscript><img alt="loading" src="/spinner.gif" decoding="async" data-nimg="fixed" style="position:absolute;top:0;left:0;bottom:0;right:0;box-sizing:border-box;padding:0;border:none;margin:auto;display:block;width:0;height:0;min-width:100%;max-width:100%;min-height:100%;max-height:100%" loading="lazy"/></noscript></span><h1>Please wait</h1></div></div><script id="__NEXT_DATA__" type="application/json">{"props":{"pageProps":{}},"page":"/","query":{},"buildId":"rYCyJCt1arYy2bGtPH3t1","nextExport":true,"autoExport":true,"isFallback":false,"scriptLoader":[]}</script></body></html>So, I separated the lines for easier viewing.
<!DOCTYPE html><html><head><meta charSet="utf-8"/>
<meta name="viewport" content="width=device-width"/>
<title>Wellcome</title><meta name="next-head-count" content="3"/>
<link rel="preload" href="/_next/static/css/a6cd15749f8dde69.css" as="style"/>
<link rel="stylesheet" href="/_next/static/css/a6cd15749f8dde69.css" data-n-g=""/>
<noscript data-n-css=""></noscript>
<script defer="" nomodule="" src="/_next/static/chunks/polyfills-c67a75d1b6f99dc8.js"></script>
<script src="/_next/static/chunks/webpack-59c5c889f52620d6.js" defer=""></script>
<script src="/_next/static/chunks/framework-7751730b10fa0f74.js" defer=""></script>
<script src="/_next/static/chunks/main-591bb7ec51acdc0d.js" defer=""></script>
<script src="/_next/static/chunks/pages/_app-1a336683ff51f334.js" defer=""></script>
<script src="/_next/static/chunks/345-9778382fb4c87e41.js" defer=""></script>
<script src="/_next/static/chunks/pages/index-461061f438c1bc00.js" defer=""></script>
<script src="/_next/static/rYCyJCt1arYy2bGtPH3t1/_buildManifest.js" defer=""></script>
<script src="/_next/static/rYCyJCt1arYy2bGtPH3t1/_ssgManifest.js" defer=""></script>
</head><body><div id="__next"><div class="text-center loading-fast">
<span style="box-sizing:border-box;display:inline-block;overflow:hidden;width:100px;height:100px;background:none;opacity:1;border:0;margin:0;padding:0;position:relative">
<img alt="loading" src="data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7"
decoding="async" data-nimg="fixed" style="position:absolute;top:0;left:0;bottom:0;right:0;box-sizing:border-box;padding:0;border:none;margin:auto;display:block;width:0;height:0;min-width:100%;max-width:100%;min-height:100%;max-height:100%"/>
<noscript><img alt="loading" src="/spinner.gif" decoding="async" data-nimg="fixed" style="position:absolute;top:0;left:0;bottom:0;right:0;box-sizing:border-box;padding:0;border:none;margin:auto;display:block;width:0;height:0;min-width:100%;
max-width:100%;min-height:100%;max-height:100%"
loading="lazy"/></noscript>
</span><h1>Please wait</h1></div></div>
<script id="__NEXT_DATA__" type="application/json">{"props":{"pageProps":{}},"page":"/","query":{},"buildId":"rYCyJCt1arYy2bGtPH3t1","nextExport":true,"autoExport":true,"isFallback":false,"scriptLoader":[]}</script></body></html>OSINT Investigation
In this section, I will conduct an OSINT investigation of this Smishing campaign. I will look at the trends on Twitter to see how people and organizations are reacting to this campaign.
Smishing Campaign Trends on Twitter
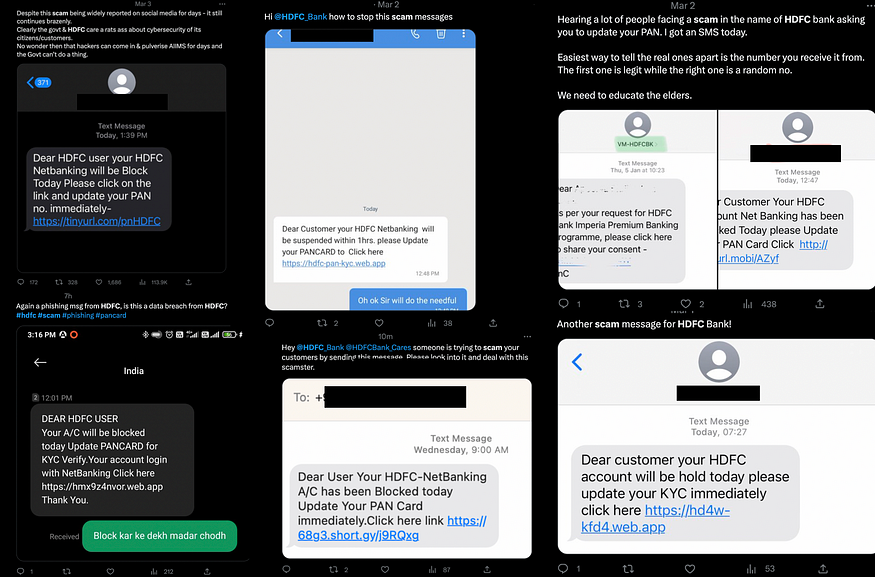
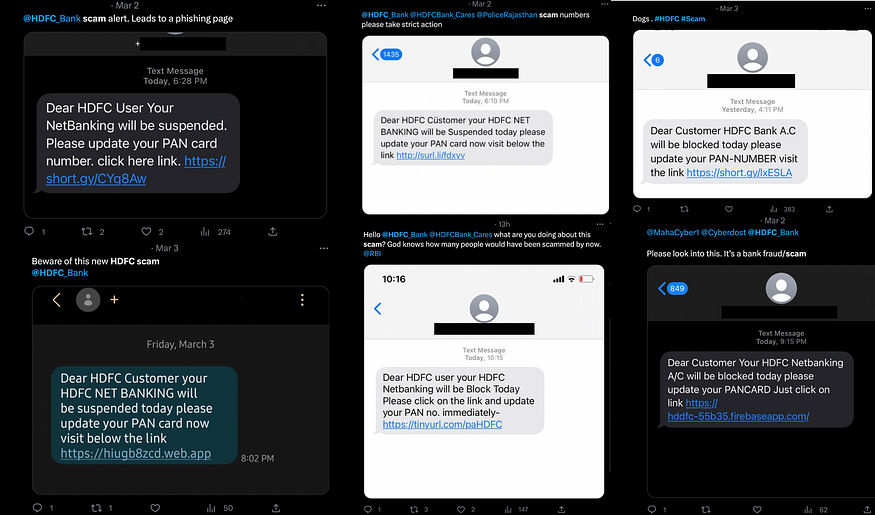
I used the search query “HDFC scam” and “Fake HDFC” on Twitter,
A lot of Tweets with a similar pretext came up. Most of them were between late February to early March.
There were different variations of the Smishing text. There were also variations in the URL shorteners, such as tinyurl, short.gy, surl.li. Some directly included the web.app link without a URL shortener.
There were different variations of the Smishing text. There were also variations in the URL shorteners, such as tinyurl, short.gy, surl.li. Some directly included the web.app link without a URL shortener.
Fake Twitter Accounts
There were even fake HDFC Bank Twitter accounts going around pretending to “Support” those who received the Smishing message.
It asks the victim to call a phone number for “assistance”. There were multiple fake HDFC Bank accounts, and there were multiple “Helpline” numbers.
It asks the victim to call a phone number for “assistance”. There were multiple fake HDFC Bank accounts, and there were multiple “Helpline” numbers.
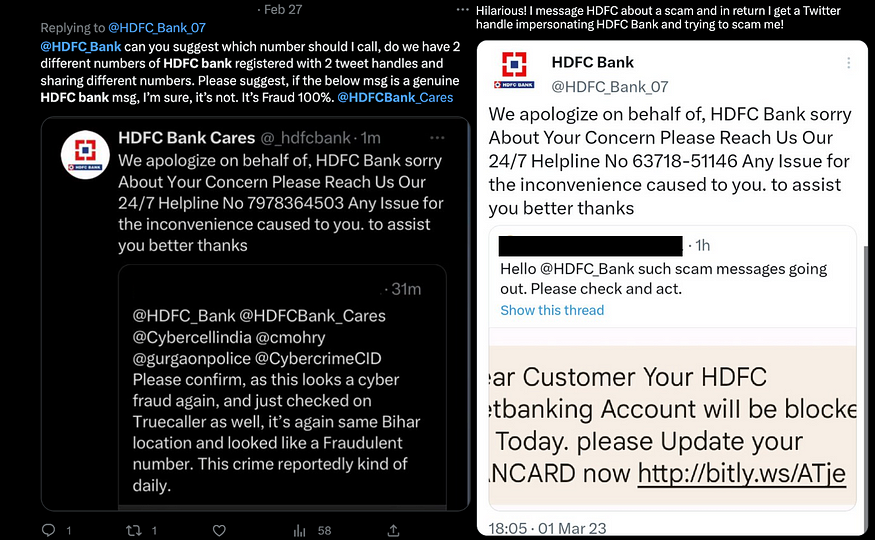
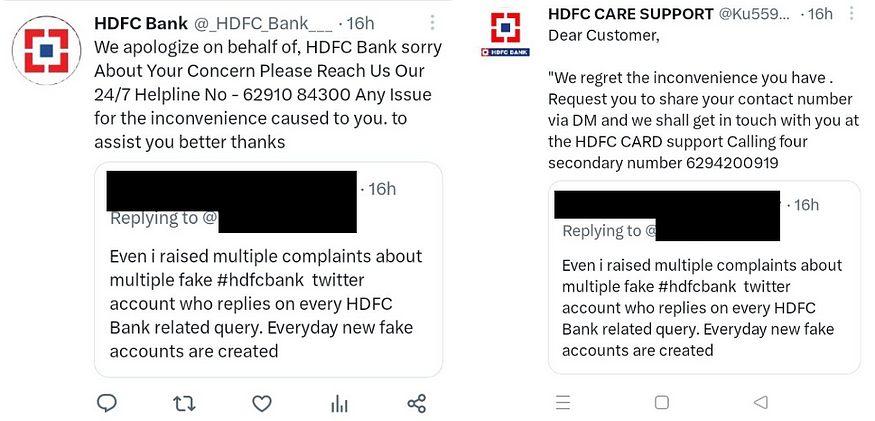
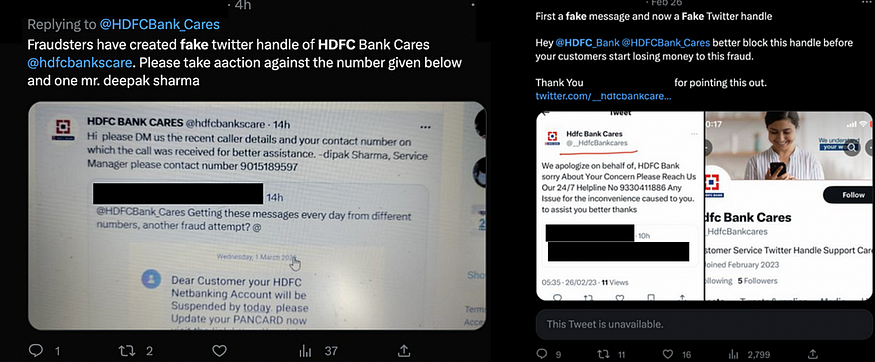
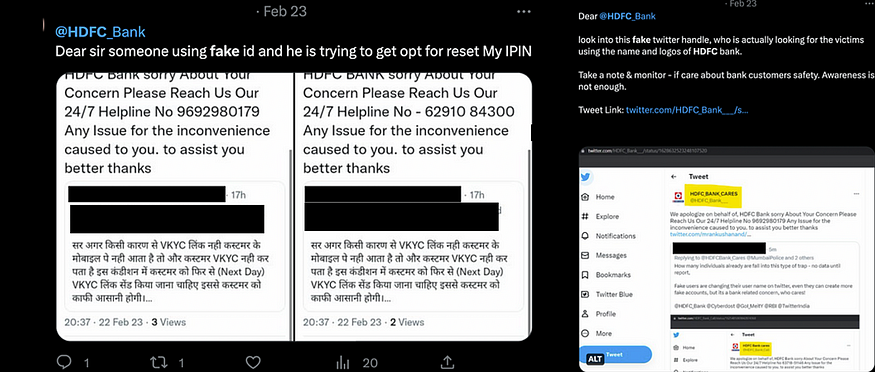
After Tweeting about my investigation of this Smishing Campaign, I received a response from a fake account:

Some fake Twitter accounts we found:
@hdfcbankscare
@__HdfcBankcares
@_hdfcbank
@HDFC_Bank_07
@_HDFC_Bank___
@HDFC_Bank___
@HDFC_SUPPORT_
@HDFC_HDFC
@hdfcbankscare
@__HdfcBankcares
@_hdfcbank
@HDFC_Bank_07
@_HDFC_Bank___
@HDFC_Bank___
@HDFC_SUPPORT_
@HDFC_HDFC
Official HDFC Bank Responses
In the official account for HDFC Bank, it mentions that @HDFCBank_cares handles queries and complaints.

We saw that @HDFCBank_cares has mentioned that official HDFC messages will always be under the hdfcnk.io domain.
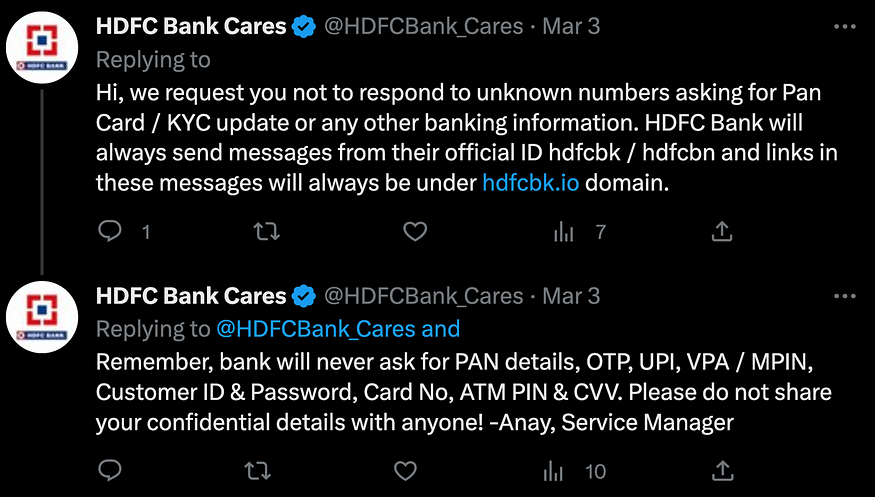
Therefore, I can judge that anything in messages that is not under the hdfcnk.io domain is not legitimate.
The official account has also clarified that there are fake HDFC Bank Support accounts going around providing fake support.
The official account has also clarified that there are fake HDFC Bank Support accounts going around providing fake support.
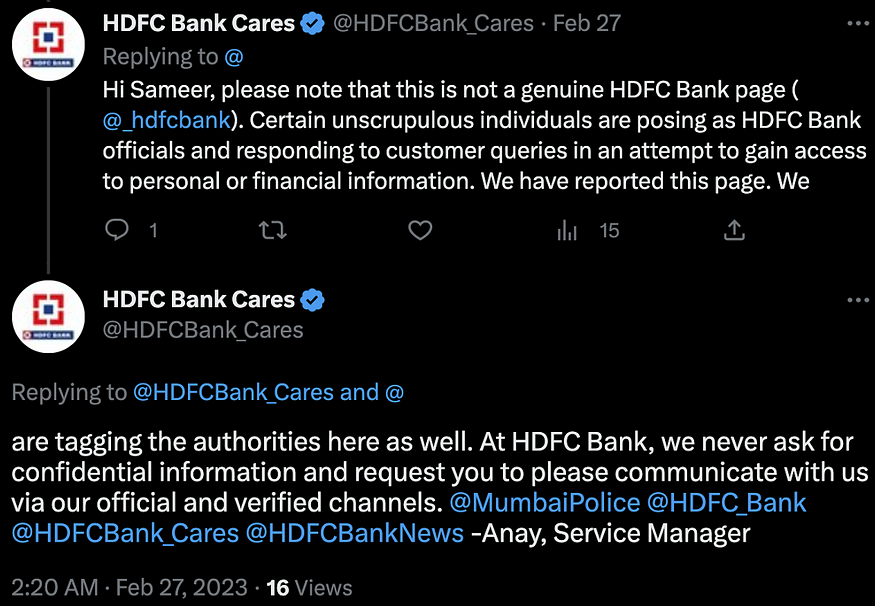
They have also made clarifications of how an authentic HDFC Bank message looks like in the following Tweet.

Threat Intelligence
This Phishing attack utilized Web.app, so we will be looking at the Threat Intelligence of Web.app through the information available online.
What is Web.app?
According to ZScaler’s “Phishing attacks abusing appspot.com and web.app domains on Google Cloud”,
Web.app is a mobile platform used for building mobile apps hosted by Firebase, which is Google’s mobile app platform.
These campaigns use SSL certificates issued by Appspot.com and Web.app, and they have well-designed login pages that attempt to spoof popular brands widely used in business, such as Dropbox Business, Microsoft Outlook and SharePoint, and DocuSign. They are designed to capture login credentials, which are sent to a remote server.
Some examples of Web.app hosted phishing pages can be seen,
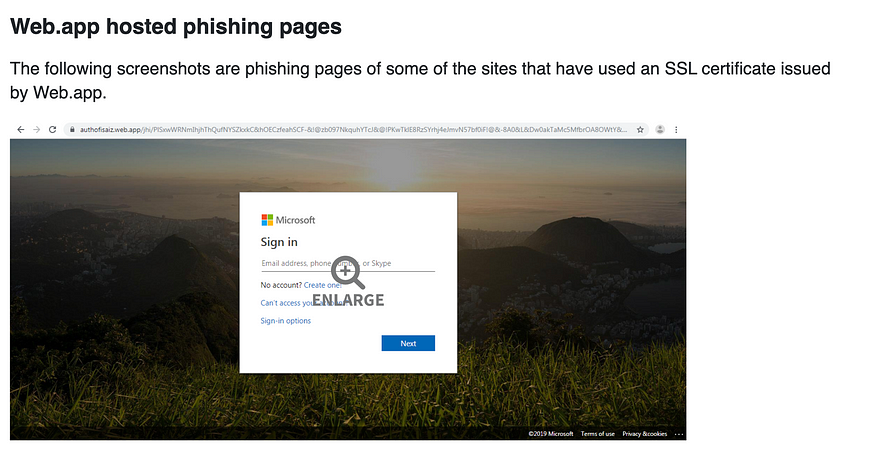
According to Cyware’s “Threat actors abuse Google domains appspot.com and web.app in latest phishing attacks”,
To evade detection, the attackers are leveraging most of the code written in an external JavaScript code.
“The attackers are using the latest tactics to evade detection from scan engines, with most of the code written in an external JavaScript file. This filename is 32 characters long and different for every site,” researchers noted.
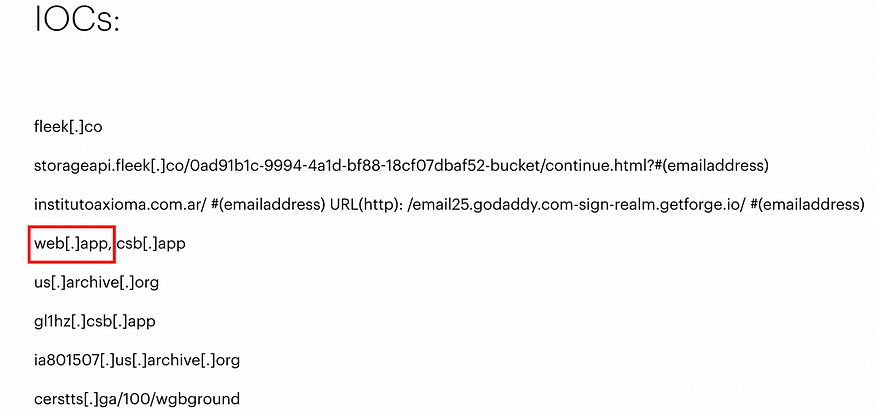
According to Resecurity, the IOCs for “LogoKit Update — The Phishing Kit Leveraging Open Redirect Vulnerabilities” includes Web.app.
From Threat Intelligence, we can see that Web.app itself is not malicious, but it is often abused and is currently widespread as it evades detection.
A Few Days Later…
I did the investigation on March 4~5 2023. I checked the status of the Reputation checkers, Phishing site, and Twitter accounts on March 7, 2023, and documented them in this section.
Reputation Status
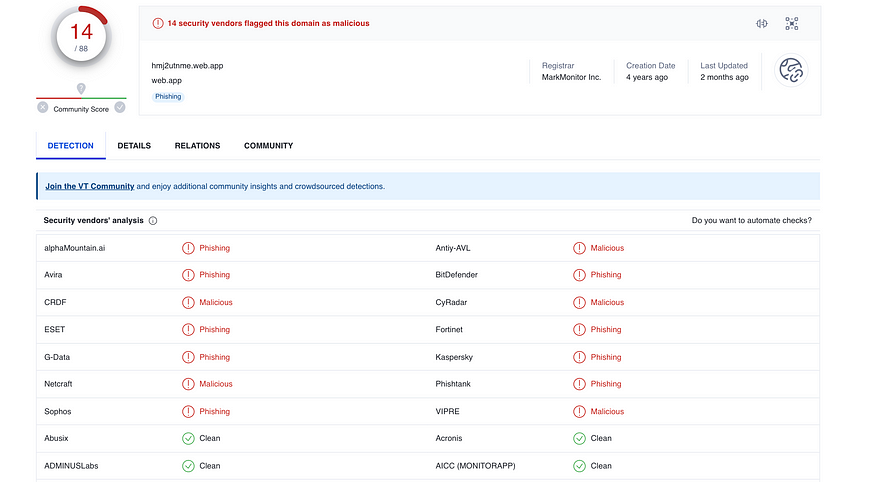
I checked the reputation status of https://hmj2utnme[.]web.app on urlscan.io and VirusTotal on March 7, 2023. More vendors have flagged it as malicious.
Phishing Site Status
I checked the https://t[.]ly/HEVC, and it was taken down by the Link Unshortener.
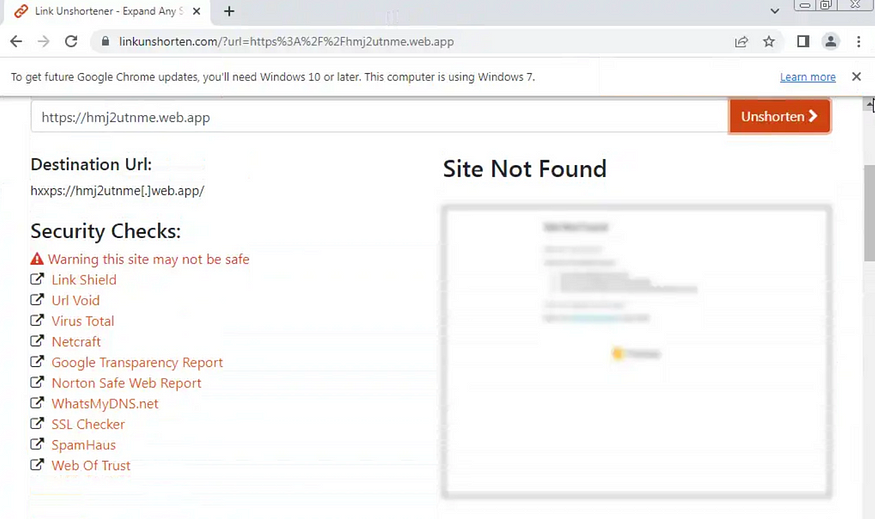
I checked https://hmj2utnme[.]web.app. This was taken down as well.
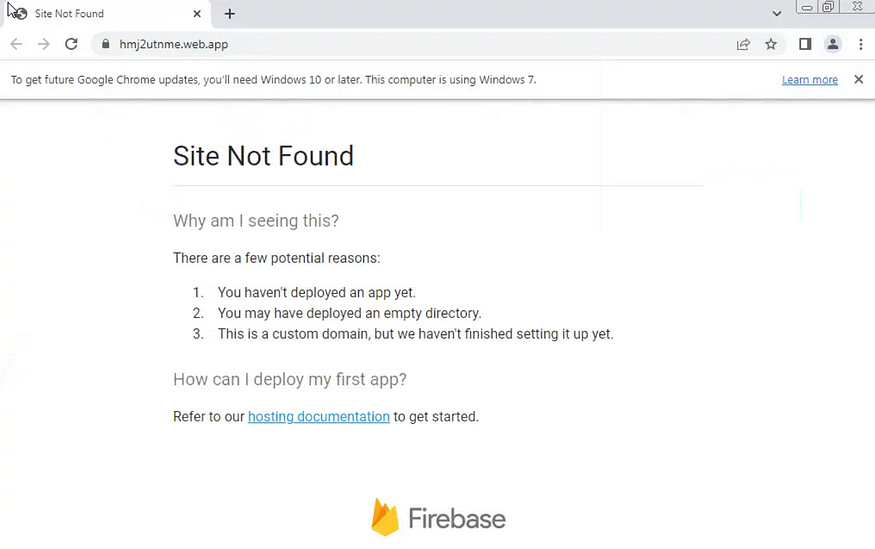
Fake Twitter Account Status
On March 7, 2023, I checked the status of the fake Twitter accounts. Most of them were suspended.
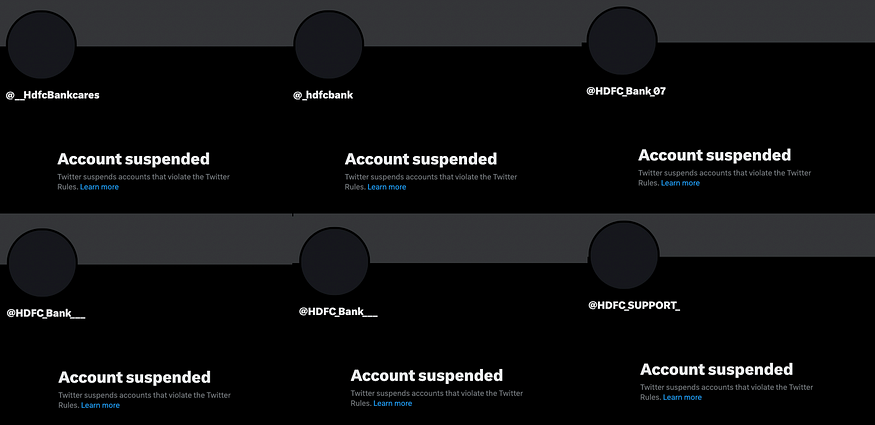
However, some of them were still active.

Saving the Evidence
The lifespan of Phishing Sites may be short, and the fake accounts may be suspended, so it may be a good idea to save some of the evidence. I will cover the use of the Internet Archive.
Internet Archive
I assumed this Phishing Site may eventually get taken down, so I saved the Phishing Site on the Internet Archive before it got taken down. This way, I can still view the Phishing Site even if it gets taken down.
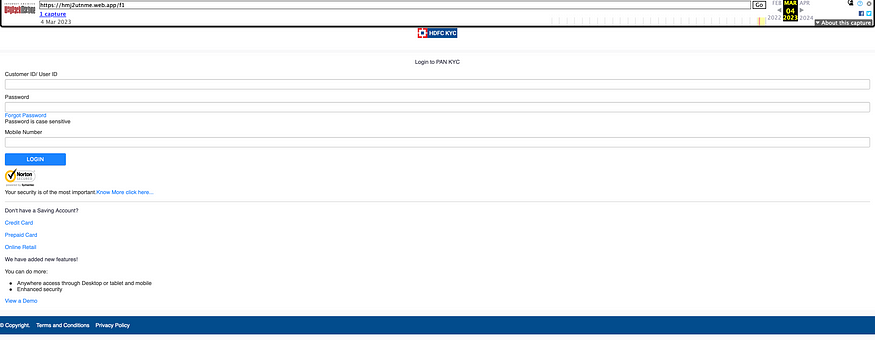
The Internet Archive sample can be found below,
https://web.archive.org/web/20230304140736/https://hmj2utnme.web.app/f1
I also saved the fake Twitter accounts on the Internet Archive before they got suspended. This way, I can still view the Tweets of the fake Twitter accounts even if it gets suspended.
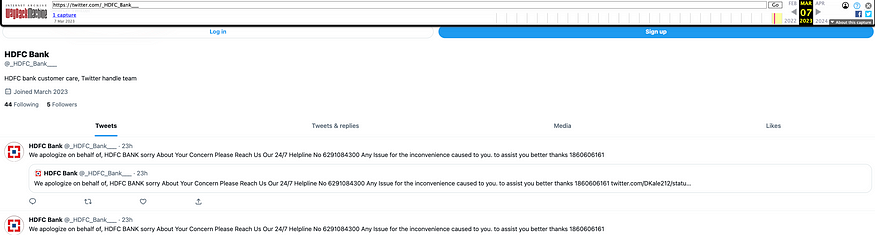
Conclusion
In conclusion, this HDFC Bank smishing campaign was widespread in India around the time of this investigation (March 4~5, 2023).
There were multiple variations in the Smishing text, and it utilized different URL shorteners or included a direct link to the Phishing page.
From the Sandbox investigation, I found that the phishing page abused Web.app, and pretended to be a fake HDFC page that asked for various information like User ID, Mobile Number, Password, Account Holder Name, Date of Birth, One Time Password, Account Number, PAN Card Number, Card Expiry Date, ATM PIN, etc. I also saw that there are POSTs to https://ns2.9appsdownload[.]org/store.php whenever information is submitted.
From the OSINT investigation, I found out that the threat actors also use OSINT for their attacks. I found that the fake HDFC Twitter accounts provided fake support to those who Tweeted about the Smishing text on Twitter. They asked those who received the Smishing text to call a “Support” number. The official HDFC has made clarifications on how authentic HDFC Bank texts look on their Twitter.
Through threat intelligence, I could see that Web.app itself is not malicious, but is often abused for malicious purposes as it evades detection.
The Phishing site investigated in this article was eventually taken down after we finished the investigation. Most of the fake Twitter accounts were suspended as well. In cases like this, it is beneficial to conduct the investigation while the scam is happening. It may also be a good idea to save the page on the Internet Archive, so we can come back to it later.
About the Author
Lena Yu is a Cybersecurity Analyst from Japan. She conducts Cybersecurity research, investigations and writes articles as a hobby. Her passion includes hacking, engineering, investigations, nature and drawing.









